Review of Bypass, Accept, or Allow Lists
Efficacy Guide using Cisco Secure Email
Scrub Existing Bypass, Accept or Allow Lists
- Host Access Table (HAT)
From your Gateway/Cloud Gateway, review Mail Policies > HAT Overview- Are there Sender Groups for "Bypass," "Accept," and "Allow"?
- Review the Sender Lists for these policies
Specifically, ALL Mail Flow Policies that have the behavior of Accept.
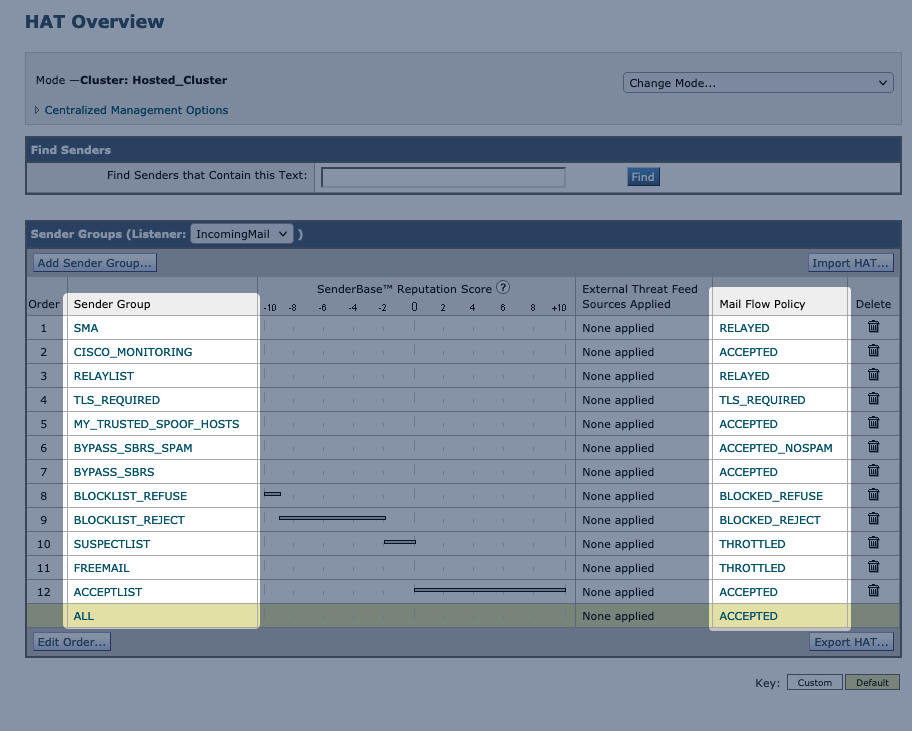
Note: Cluster: Hosted_Cluster as this is Cloud Gateway
-
Exceptions Table
From your Gateway/Cloud Gateway, review Mail Policies > Exception Table- Are there any exceptions and behaviors?
- Review and purge as needed
-
Address Lists
From your Gateway/Cloud Gateway, review Mail Policies > Address Lists- Are there Address Lists active for DMARC or named "Bypass"?
- Review and purge as needed
-
Forged Email Detection (if enabled)
From your Gateway/Cloud Gateway, review Mail Policies > Dictionaries- Review and scrub "Allowed" or dictionaries that contain email addresses, domain names
- Review Mail Policies > Incoming Content Filters
- Select 'Rules' and, using your browser search, search for any matching dictionary names associated with the step above. Review and confirm Conditions and Actions.
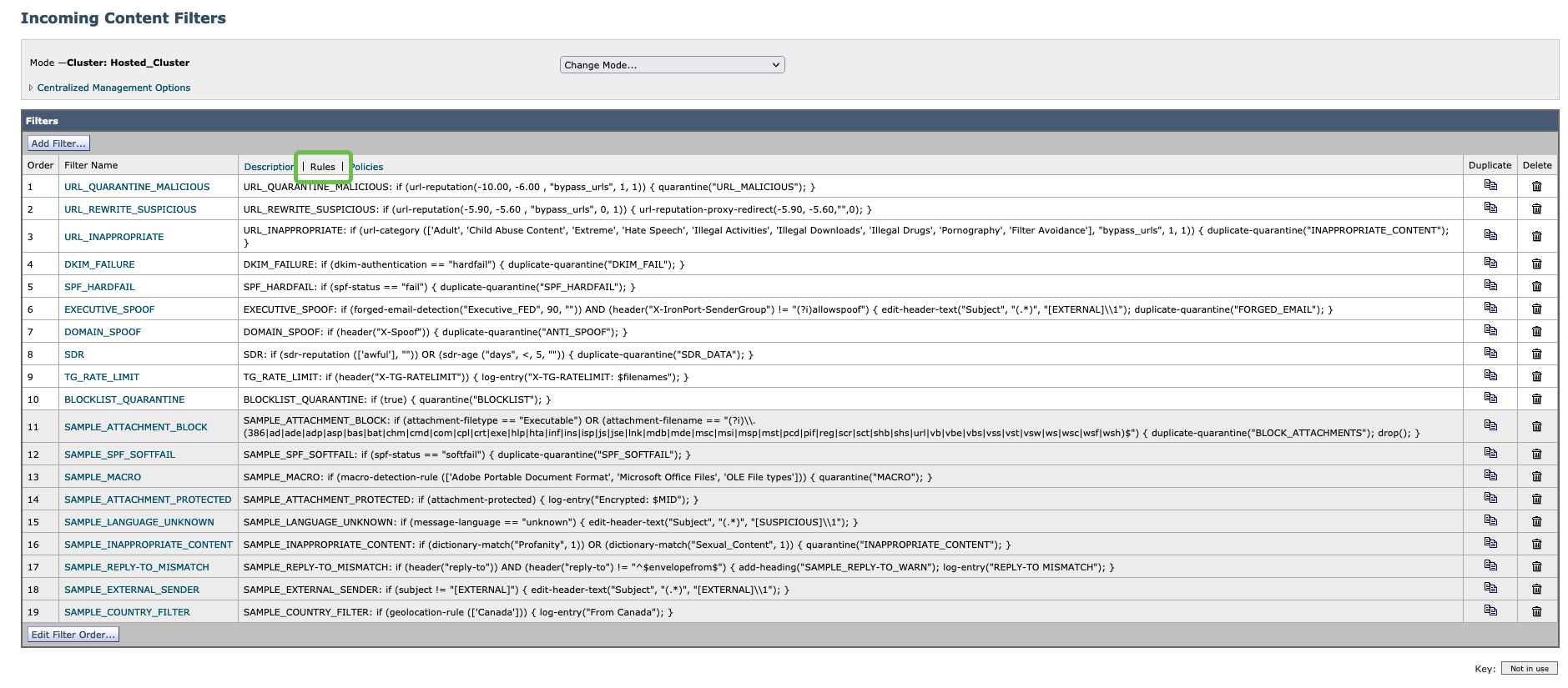
Note: Cluster: Hosted_Cluster as this is Cloud Gateway
Guide Checklist
At this time, we have completed the following:
- Introduction
- Validate Detection Services
- Review of Bypass, Accept or Allow Lists
- Aggressive Profile for Anti-Spam
- Review and Validate MX Records
- Submissions to Talos
- Support Requests
- Security Review (Optional)
Once you have completed the review and any changes to your Bypass, Accept, or Allow Lists, proceed to the next section of this document.
Updated about 2 years ago
What’s Next
