Site-to-Site VPN
Cisco Secure Email Cloud Gateway
Cisco offers a site-to-site VPN tunnel for Cloud Gateway customers. The VPN tunnel facilitates non-SMTP services such as LDAP lookups for a recipient, log transfers (Syslog) and user authentication, and RADIUS for two-factor authentication.
How to request a site-to-site VPN
Please complete the following sign-up form:
VPN tunnel is NOT for SMTP traffic.
RADIUS for external authentication of administrator accounts is not available at this time.
VPN tunnel is available at no cost to customers!
General VPN Information
The VPN will leverage a shared RFC 1918 IP space of your choosing to create the VPN tunnel. This tunnel can be used for LDAP lookups for a recipient, log transfers (Syslog), and user authentication, RADIUS authentication.
SMTP and HTTPS traffic will still need to proceed via the internet for logging and inspection purposes.
Each customer will have two (2) tunnels, one for each data center, that is statically routed. Pre-shared keys will be communicated out-of-band to the customer in an encrypted email via the Cisco Registered Envelope Service (RES).
The tunnel leverages IKEv1 & IKEv2.
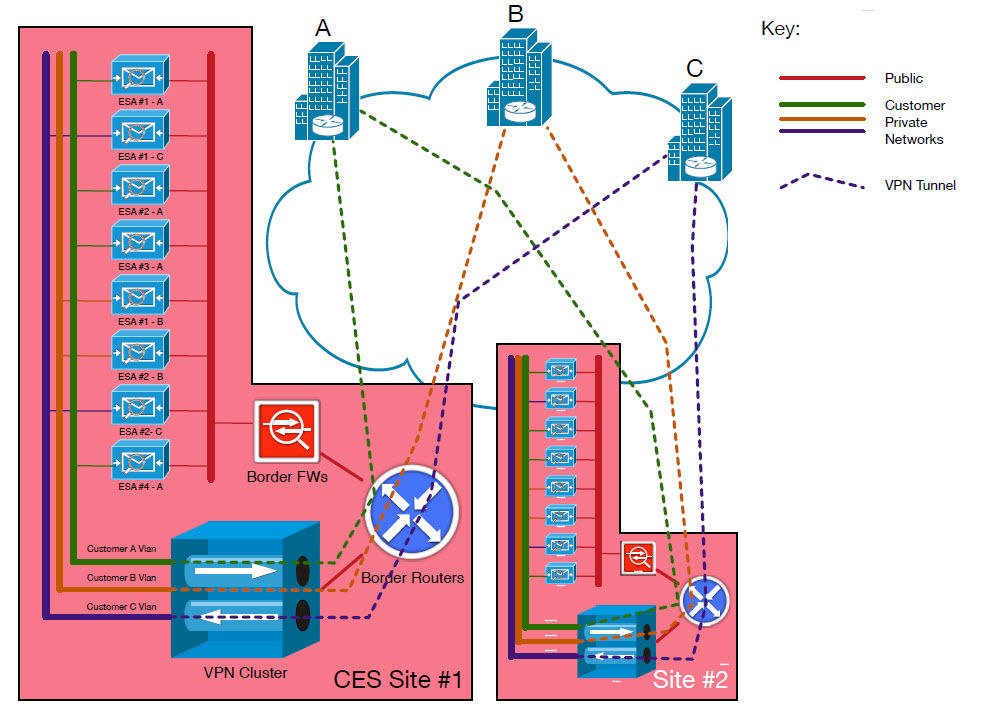
Figure 1 - Customer VPN Topology
The figure above shows three customers, A, B, and C. Virtual routing and forwarding (VRF), VLANs, and tunnels are color-coded.
Within each CES site, a private VLAN is assigned to each customer, and an isolated routing VRF is created on an ASR-based router cluster. RFC1918 IPs are assigned and static routes are placed on the ESAs to communicate with the on-premises services.
This network is completely separate from the public VRF used for sending and receiving mail, with separation enforced at the VLAN tagging level. Private networks are non-routable within CES anywhere outside the private VRF on the VPN cluster.
VPN Settings
1️⃣ Phase1
IKEv1 (Default)
crypto isakmp policy 30
authentication pre-share
encryption aes 256
hash sha
group 5
lifetime 86400
crypto isakmp policy 20
encr aes 256
hash sha384
authentication pre-share
group 14
lifetime 86400
crypto isakmp policy 30
encr aes 256
hash sha
authentication pre-share
group 14
lifetime 86400
The Group 5 profile is considered "legacy" but supported by nearly all clients, customers with newer hardware can use group 14; the reason for the two policies is the ASA/FTP firmware only supports sha-1 for IKEv1, routers support sha-2 (sha384).
IKE lifetime mismatches should be okay as long as the customer's lifetime is significantly longer than the phase2 lifetime of 3600; during negotiation, they should agree to use the lower value.
PFS
Default is no PFS. PFS can be enabled with group5 or group14.
IKEv2 (as of 3 Feb 2021)
The routers are set up with a very flexible default phase1 profile set:
crypto ikev2 proposal CES_DEFAULT
encryption aes-cbc-256 aes-cbc-192 aes-cbc-128 3des
integrity sha512 sha384 sha256 sha1 md5
group 14 5 2
Basically, a client that uses any of these encryption, integrity, and group settings should be able to negotiate.
2️⃣ Phase2
IPsec Transform set
Currently, the default is:
esp-aes 256 esp-sha-hmac
The automation supports setting several other alternative sets, among those configured:
- esp-aes esp-sha-hmac (Some older ASA code bases do not support the 256 specifier)
- esp-aes 256 esp-sha384-hmac (SHA2 384 bit for auth)
Need help with VPN and setup/configuration?
- You can open a TAC case for assistance with the setup and configuration of the VPN tunnel:
Cisco Support & Downloads
Updated about 2 years ago
