URL Filtering
URL Defense Guide using Cisco Secure Email
URL Filtering
URL Filtering allows message and content filters to take action based on the reputation or category of URLs in messages.
URL Filtering Prerequisites
In addition to enabling URL filtering, it is recommened to enable other features depending on desired functionality.
For enhanced protection against spam:
- Anti-spam scanning must be enabled globally and per applicable mail policy. This can be either the IronPort Anti-Spam or the Intelligent Multi-Scan feature.
For enhanced protection against malware:
- The Outbreak Filters feature is recommended to be enabled globally and per applicable mail policy. In order to utilize URL Category and URL Reputaion conditions and actions in Message and Content Filters, or URL Rewriting (option in Outbreak Filters), the feature has to be enabled.
- Message and Content Filters need to have an action configured, based on URL reputation, to enforce acceptable use policies.
Cisco Secure Email provides URL defense via URL Filtering in the following ways:
- Message Filters
- URL Category
- URL Reputation
- Content Filters
- URL Category
- URL Reputation
- URL Allowed Lists
- Web Interaction Tracking
The Context Adaptive Scanning Engine (CASE) is the main driver of URL Filtering on the email gateway. CASE, URL reputation, and category are provided by cloud-based Talos Intelligence Services.
Message Filters and Content Filters
- Message filters are applied before per-policy scanning occurs in the email pipeline.
- Content filters are similar to message filters, except that they are applied later in the email pipeline — after message filtering after a message has been “splintered” into a number of separate messages for each matching mail policy, and after the message has undergone anti-spam and anti-virus scanning.
Message Filters
This document will not cover message filters. For more information, see the “Detecting Malicious URLs in Messages Using Message Filter” chapter of the user guide.
URL Category
The category of URLs (for example, Adult Content or Illegal Activities) can be used in conjunction with content and message filters to enforce corporate acceptable use policies. (See the FAQ.)
URL Reputation
| URL Reputation | Score Range | Description |
|---|---|---|
| Untrusted | -10.0 to -6.0 | Displays a behavior that is exceptionally bad, malicious, or undesirable. |
| Questionable | -5.9 to -3.1 | Displays behavior that may indicate risk, or undesirable. |
| Neutral | -3.0 to 0.0 | Does not display positive or negative behavior. However, this verdict has been evaluated. |
| Favorable | 0.1 to 5.9 | Displays behavior that indicates a level of safety. |
| Trusted | 6.0 to 10.0 | Displays behavior that indicates exceptional safety. |
| Unknown | Not previously evaluated, or lacking features to assert a threat level verdict |
Cisco Talos URL Reputation Scoring
For direct info, please see: Announcement for URL Reputation Verdict Name Changes in Cisco Email Security Gateway
URL Allowed Lists
If you specify a global allowed list when configuring the URL Filtering feature, then URLs on the allowed list are not evaluated for reputation or category, for anti-spam, Outbreak Filtering, or content and message filtering. However, the messages that contain these URLs are evaluated as usual by anti-spam scanning and Outbreak Filters. You can also specify a URL-allowed list in each URL Filtering condition (rule) and action in content and message filters, to supplement the global URL-allowed list.
To categorize allowed list URLs from Outbreak Filtering generally, use the Bypass Domain Scanning option that you configure on the Mail Policies: Outbreak Filters page. URL-allowed lists for URL filtering are similar to but independent of, Bypass Domain Scanning. For more information about that feature, see URL Rewriting and Bypassing Domains.
Web Interaction Tracking
The web interaction tracking feature provides information about the end users who clicked on rewritten URLs and the action (allowed, blocked, or unknown) associated with each user's click. Once you enable this feature, you can use the Web Interaction Tracking report to view information such as the top malicious URLs clicked, top users who clicked on malicious URLs, and so on.
External Threat Feeds
External Threat Feeds (ETF) can also be configured on the email gateway to provide Indicators of Compromise. The ETF framework allows the email gateway to consume external threat information in STIX format communicated over the TAXII protocol. Similar to what CASE provides, the following is a list of STIX Indicators of Compromise (IOCs) supported:
- File Hash Watchlist (describes a set of hashes for suspected malicious files)
- IP Watchlist (describes a set of suspected malicious IP addresses)
- Domain Watchlist (describes a set of suspected malicious domains)
- URL Watchlist (describes a set of suspected malicious URLs)
For the purposes of this document, we will focus on URLs.
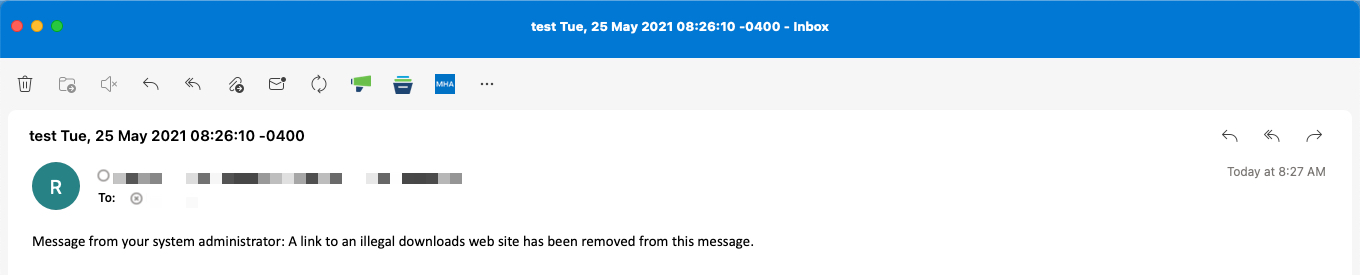
Using Content Filters
Checks URLs within: Message Body & Subject, Attachments, Both
For conditions, the email administrator can choose to configure the message body and subject, attachments, or all, when evaluating URLs that are contained in messages processed through the email gateway
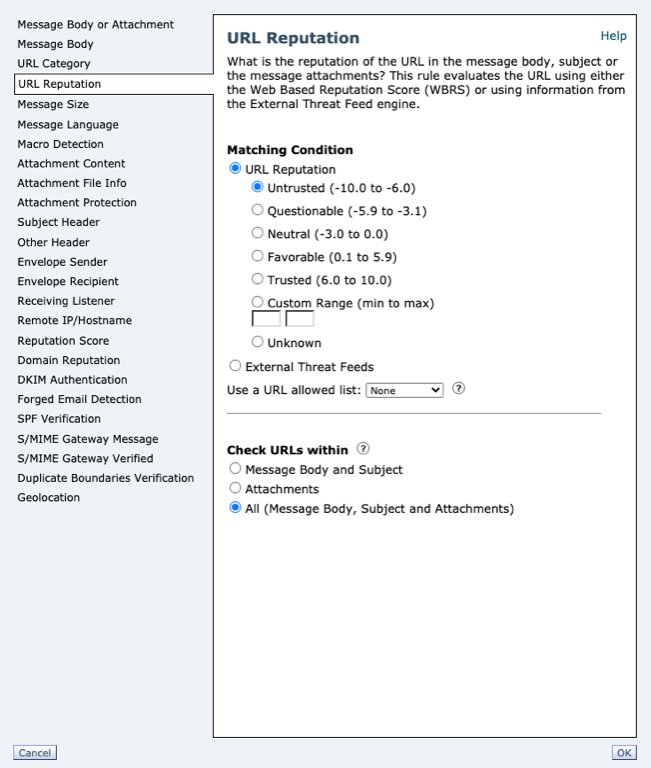
Action on URL: Defang, Redirect to Cisco Security Proxy, Replace URL with a text message
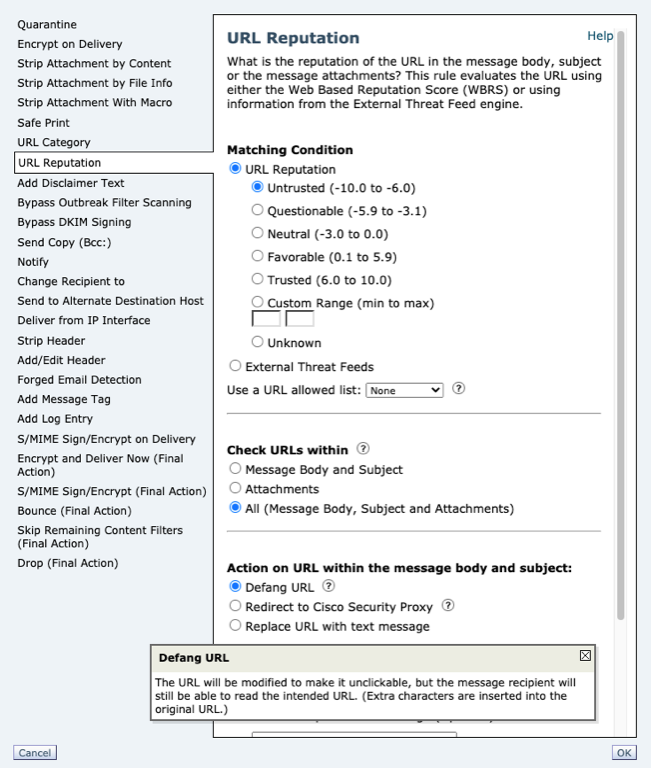
Defang
For actions set to use Defang, the URL will be modified to make it un-clickable, but the message recipient will still be able to read the intended URL. (Extra characters are inserted into the original URL.)
| What does this look like for the end-user? |
|---|
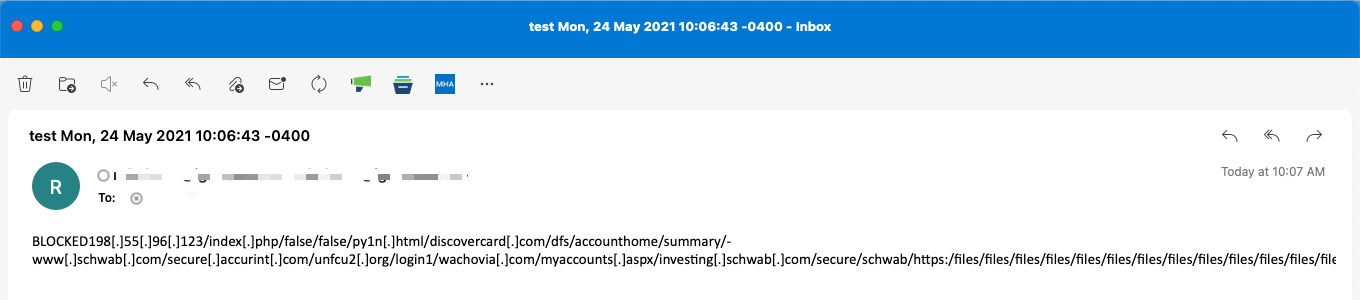
Click the image to enlarge
Redirect to Cisco Security Proxy
For actions set to use Redirect to Cisco Security Proxy, the URL will be rewritten to pass through Cisco's Security Proxy for additional verification when clicked. Based on Security Proxy's verdict, the user may not be able to access the site.
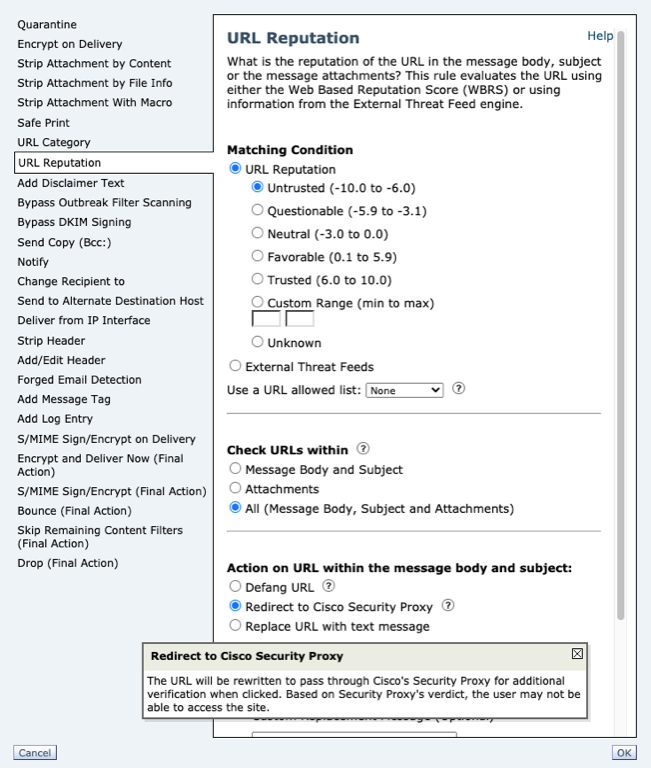
| What does this look like for the end-user? |
|---|
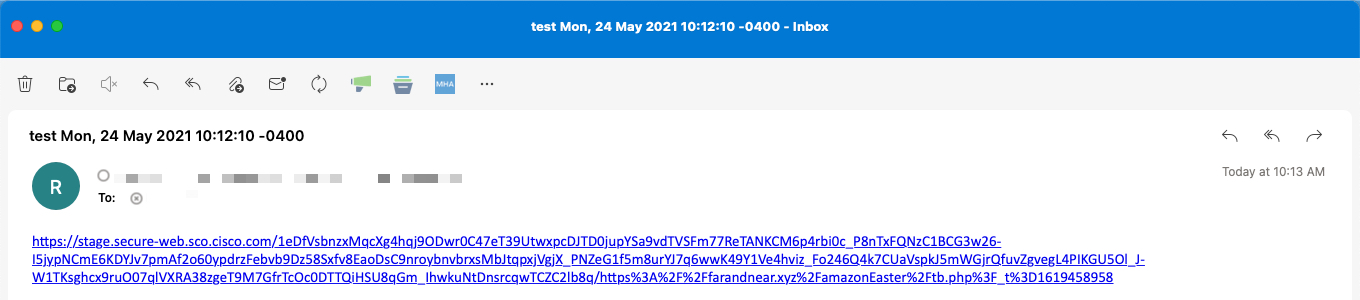
Click the image to enlarge
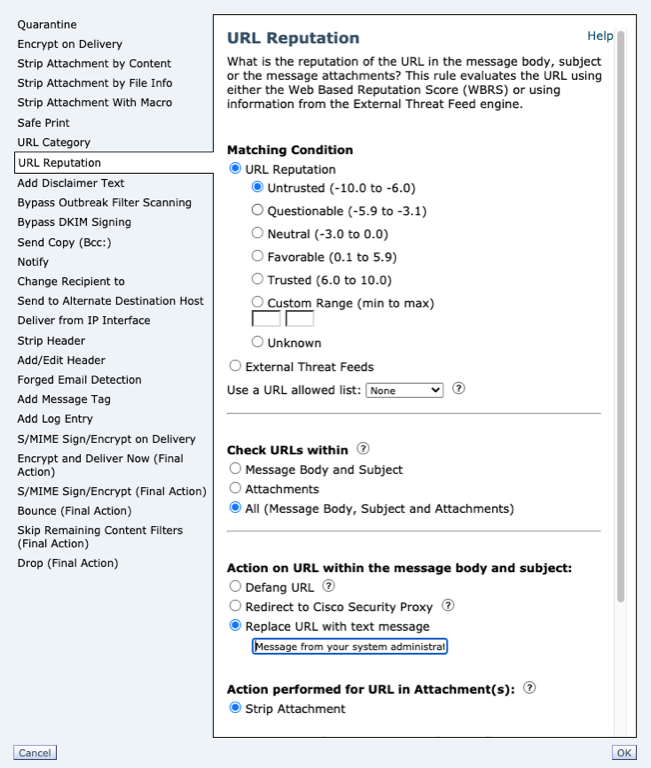
Replace URL with a text message
For actions set to Replace URL with text message, replace the URL with any text.
- To include the original URL in the text that appears in the message, use the $URL variable.
- Examples:
- Replace all URLs in the Illegal Downloads category with a note:
Message from your system administrator: A link to an illegal downloads web site has been removed from this message.
| What does this look like for the end-user? |
|---|
Click the image to enlarge
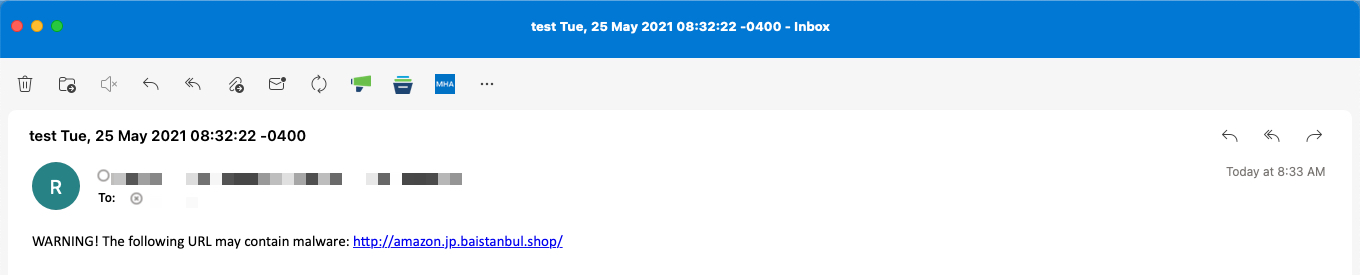
Replace and use the $URL variable
To include the original URL along with a warning, use the following example:
WARNING! The following URL may contain malware: $URL
| What does this look like for the end-user? |
|---|
Click the image to enlarge
Action on URL: Replace URL with a text message can also use Remote Browser Isolation
Taking a combination approach with what was described above, you can utilize your host or external services to redirect URLs to a custom proxy or web security service:
http://<custom_proxy_hostname/IP>/$URL
| What does this look like for the end-user? |
|---|
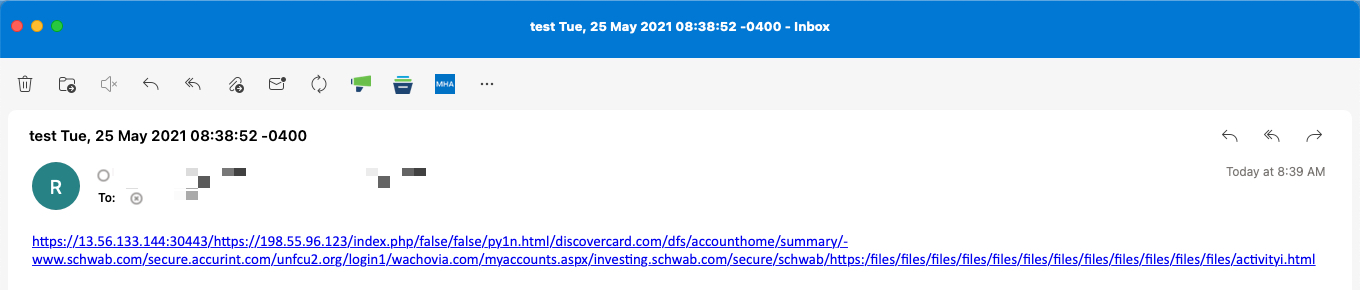
Click the image to enlarge
You will be responsible for the Remote Browser Isolation host and utilization for the URL detonation when selecting to send the URL to your own proxy.
URL Filtering In-depth
For more information, see the “Protecting Against Malicious or Undesirable URLs” chapter of the user guide.
Updated about 2 years ago
