Cisco Secure Email Add-in FAQ
Cisco Secure Email Add-in FAQ
Do I need a license for either add-in? What is the cost of the add-ins?
Neither add-in requires any additional licensing to download or use. Both are free for Cisco Secure Email customers. You will need a Cisco ID (CCO ID) to download the Submission Add-in. For the Encryption Add-in, you will need to have an existing Cisco Secure Email Encryption Service account and administrator access.
Technical support for Submission Add-in and Encryption Add-in?
Cisco customers can engage Cisco TAC to open a technical support case for issues, enhancements, and other related add-ins questions.
What is the "add-in"?
- The Submission Add-in + Encryption Add-in are Microsoft Outlook integrations from Cisco that work the same across Windows and Mac, and Web (Microsoft 365). XML coding is readily deployable from stand-alone with-in Outlook or deployed quickly from Microsoft Admin Center for Microsoft 365. (For more information see Microsoft's Office Add-ins platform overview + Outlook add-ins overview.)
If I have the Cisco Secure Email Plug-in installed, do I need to uninstall it before using the add-in?
The Cisco Secure Email Plug-in is no longer supported as of Deceber 2023 and should be removed.
Please see the Supported Configurations section of the User Guide for the add-in for more information. (Note: You can install the Cisco Secure Email Encryption Service add-in only if you are using an Office 365/Microsoft 365 subscription.)
Can both add-ins run at the same time in Outlook?
Yes. Both add-ins operate separately as they provide independent functions. Submission Add-in for reporting spam, ham, missed messages to Cisco. Encryption Add-in for managing Cisco Secure Email Encryption messages directly from Outlook.
Is the Cisco Secure Email Plug-in being discontinued/End-of-Life (EoL)?
Yes. The plug-in End Of Life was December 31, 2023.
Outlook using multiple accounts?
Add-ins may be installed (when permitted) for individual email accounts within Microsoft Outlook. If you have multiple accounts configured in Outlook, be sure that you review the Add-ins directly from the toolbar when selecting an account. If the add-in is grayed out when selecting, it may not be installed or permitted for that account.
Where is the add-in configuration stored?
- These are specific to Microsoft Add-in settings, referred to as "Roaming Settings," and are stored in the user's Exchange server mailbox where the add-in is installed. Because these settings are stored in the user's server mailbox, they can "roam" with the user and are available to the add-in when running in the context of any supported Office client application or browser accessing that user's mailbox.
- Outlook add-in roaming settings are available only to the add-in that created them and only from the mailbox where the add-in is installed.
I have installed the add-in and it is not showing or updating in Outlook.
- If you have the add-in installed via Microsoft 365 Admin Center, it will take up to 12 hours for the add-in to be displayed on users' ribbons - users might need to relaunch Office.
- You may also wish to try clearing your browser cache (for OWA) or clearing your Outlook desktop client cache. (For more information, see Microsoft's Clear the Office cache.
- If you still experience any issues, please engage Cisco TAC to open a technical support case.
Submission Add-in Specific
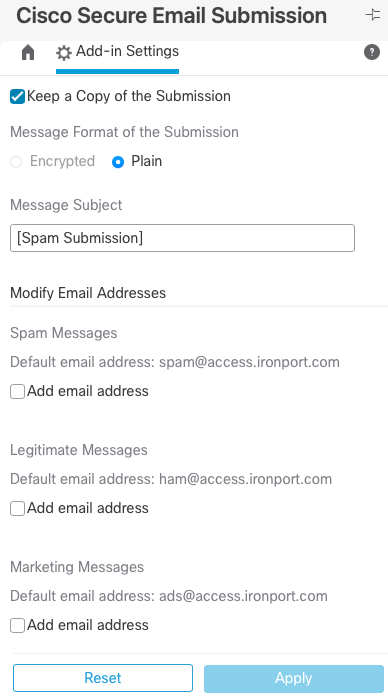
Can I submit messages to additional addresses or keep a copy of the submission?
Yes. Open the Submission Add-in and click on the 'gear' icon. You will see the options to add additional addresses.
Encryption Add-in Specific
I have already configured my ESA for Mailbox Auto Remediation/Search and Remediate with Azure, so I have an Application ID/Tenant ID for Cisco Secure Email. Can I use this for my Encryption Add-in, too?
Yes. You simply need to add a Client Secret to the existing application in your Azure app registration.
Log-in to Azure and do the following:
- Click Azure Active Directory
- Click App registrations
- Select your previously configured app
- Click Certificate & secrets in the left-hand menu, under Manage
- In Client secrets, click + New client secret
- Add a description as needed and set the expiration period and click Add
- Copy the Value output (*Note: this will "**********" out the value once you log-out of Azure)
- Log-in to your Encryption account (https://res.cisco.com/admin)
- When configuring your Add-in Config, use the Client Secret you just created
My domain email is managed from Google G-Suite and not Microsoft 365, but I use Outlook. How can I install the Encryption Add-in?
At this time the setup requires Azure AD permissions via Microsoft Graph API, G-Suite is not supported. Future updates to the Add-in may allow API setup with Google G-Suite.
For G-Suite customers, we recommend to use a header or subject modification for the emails that should be encrypted.
Do I need the Encryption Add-in to send encrypted messages through my Cisco Secure Email gateway?
No. If your organization has subject line flagging or any other Message/Content Filter triggered action to encrypt at the gateway, you can send messages still via that method. For more information on this, please see ESA Email Encryption Configuration Example.
The Add-in simply provides an alternative, easy method to flag and send encrypted messages via the Cisco Secure Email Encryption Service (formerly Cisco Registered Envelope Service).
Do you have more questions? Let us know!
Related Information
- Talos - Email Status Portal [Requires CCO log-in]
- Talos - Email Status Portal Help [Requires CCO log-in]
- Cisco Secure Email Encryption Service [End-user Access]
- Cisco Secure Email Encryption Service [Admin Access]
- (All) Cisco Secure Email Encryption Release Notes
- (All) Cisco Secure Email Encryption End-User Guides
- Outlook Plug-In End Of Life Notification
Updated almost 2 years ago
