Mailbox Auto Remediation (MAR)
Mailbox Auto Remediation on Microsoft Exchange Online, Microsoft Exchange on-premise, hybrid, and multi-tenant deployments
Looking for configuration assistance? Please see: Configuring Azure and Microsoft 365 for Mailbox Auto Remediation and Search & Remediate
A file can turn malicious anytime, even after it has reached the user’s mailbox. Cisco Secure Email's Advanced Malware Protection (AMP)[File Reputation and File Analysis] can identify this as new information emerges and push retrospective alerts to your appliance. You can configure your appliance to perform auto-remedial actions on the messages in the user mailbox when the threat verdict changes.
The appliance can perform auto-remedial actions on the messages in the following mailbox deployments:
• Microsoft Exchange Online – mailbox hosted on Microsoft Office 365
• Microsoft Exchange on-premise – a local Microsoft Exchange server
• Hybrid/Multiple tenant configuration – a combination of mailboxes configured across Microsoft Exchange Online and Microsoft Exchange on-premise deployments
For more information, see the “Mailbox Auto Remediation” guide.
There are a few changes to how this is configured on the Email Gateway. Starting with AsyncOS 13.0, MAR is now configured from System Administration > Account Settings. Previously this was configured from System Administration > Mailbox Settings
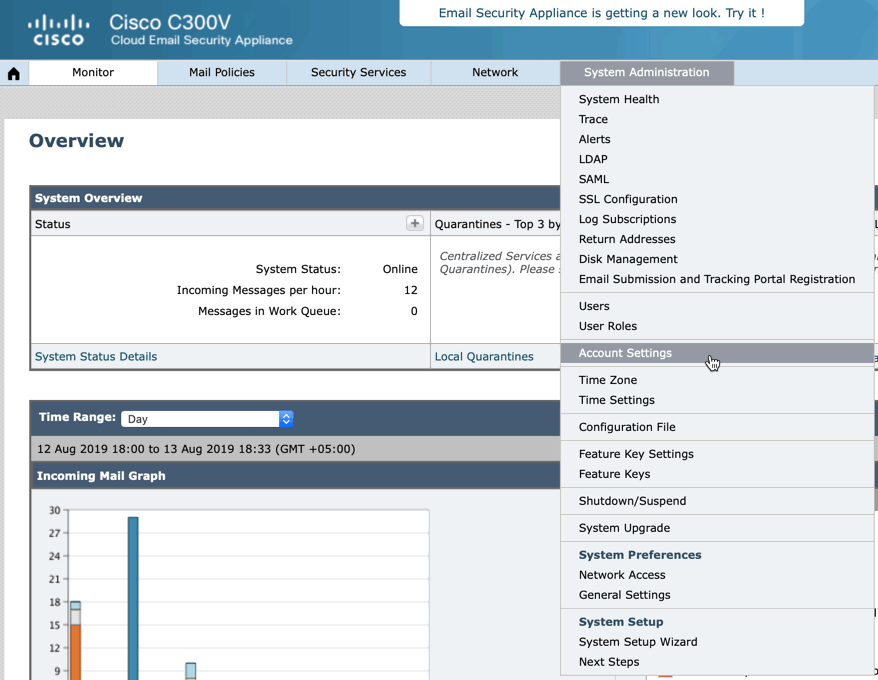
System Administration > Account Settings
For Microsoft 365 deployments, the API permissions have changed from Exchange to Microsoft Graph. Any Microsoft 365/Microsoft Azure app registration will now need to have the following API permission configured and the consent granted:
- Select Microsoft Graph
- Select the below permissions on Application permissions:
- Mail > "Mail.Read" (Read mail in all mailboxes)
- Mail > "Mail.ReadWrite" (Read and write mail in all mailboxes)
- Mail > "Mail.Send" (Send mail as any user)
- Directory > "Directory.Read.All" (Read directory data) [*Optional: If you are using LDAP Connector/LDAP synchronization, enable. If not, this is not required.]
Original Documentation for Microsoft 365 setup (utilizing Exchange API):
How-to configure Cisco Secure Email Account Settings for Microsoft Azure (Microsoft 365) API
Be sure that you are adding your Microsoft 365 domain to the "Domain Mapping" configuration. If not, you will see similar in your mar logs:
Tue Aug 13 20:12:52 2019 Info: MID: 4692 Skipping mailbox remedial action since domain map is not configured for recipient's ([email protected])domain.
Mailbox Auto Remediation Testing and Example
Cisco Secure Endpoint requires an additional license and access. Please see Cisco Secure Endpoint for more information.
With Cisco Secure Endpoint, an attachment's SHA256 can be tagged as malicious by adding them to a 'Custom Detection -Simple' policy. This will then force the Email Gateway that processed the original SHA256 to mark the file as 'malicious' and process a remediation event against the original message.
Example
AMP logs:
Tue Aug 20 06:34:27 2019 Info: File reputation query initiating. File Name = 'today_is_clean.pdf', MID = 5223, File Size = 144054 bytes, File Type = application/pdf
Tue Aug 20 06:34:27 2019 Info: Response received for file reputation query from Cloud. File Name = 'today_is_clean.pdf', MID = 5223, Disposition = LOWRISK, Malware = None, Analysis Score = 0, sha256 = 993e53a12c43a19e21c3829152d313f0abce4869e1644bc8e60522eb8e637298, upload_action = Recommended to send the file for analysis
Tue Aug 20 06:34:27 2019 Info: File not uploaded for analysis. MID = 5223, File SHA256[993e53a12c43a19e21c3829152d313f0abce4869e1644bc8e60522eb8e637298], File mime[application/pdf], Reason: No active/dynamic contents exists
The SHA256 (993e53a12c43a19e21c3829152d313f0abce4869e1644bc8e60522eb8e637298) was then added to Cisco Secure Endpoint blocklist:
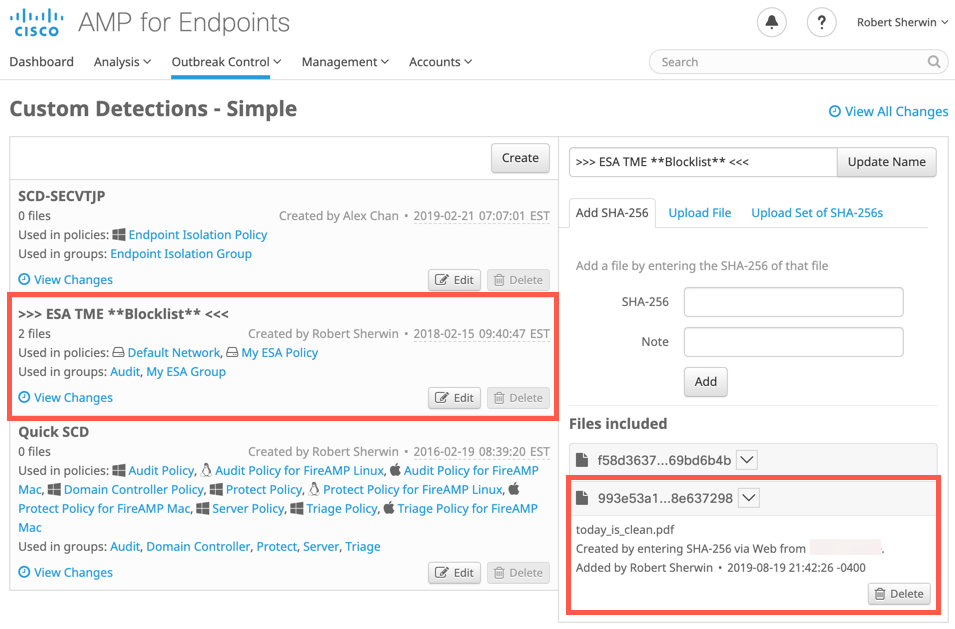
AMP logs:
Tue Aug 20 06:54:01 2019 Info: Retrospective verdict received. MID: 5223, SHA256: 993e53a12c43a19e21c3829152d313f0abce4869e1644bc8e60522eb8e637298, Timestamp: 1566266041.14, Verdict: MALICIOUS, Spyname: W32.RetroDetected
Info message is sent from the ESA to the ESA Admin:
On 8/19/19, 9:54 PM, "IronPort C300V Alert" <[email protected]> wrote:
The Info message is:
Retrospective verdict received for today_is_clean.pdf.
SHA256: 993e53a12c43a19e21c3829152d313f0abce4869e1644bc8e60522eb8e637298
Timestamp: 2019-08-20T01:54:01Z
Verdict: MALICIOUS
Spyname: W32.RetroDetected
Total users affected: 1
----------- Affected Messages ---------------
Message 1
MID : 5223
Subject : today_is_clean.pdf
From : [email protected]
To : [email protected]
File name : today_is_clean.pdf
Parent SHA256 : unknown
Parent File name : unknown
Date : 2019-08-20T01:34:27Z
---------------------------------------------------
Version: 13.0.0-252
Serial Number: 420D4F36AAEBC0093B4F-B9E72189A021
Timestamp: 20 Aug 2019 06:54:01 +0500
To learn more about alerts, visit our support community and troubleshooting site. In many cases, you can find more information about this specific alert.
For troubleshooting, see the following URL :
https://www.Cisco.com/c/en/us/support/security/email-security-appliance/products-tech-notes-list.html
For ESA Support, see the Cisco Support Community site :
https://supportforums.cisco.com/t5/email-security/bd-p/5756-discussions-email-security
If you desire further information, please contact your support provider.
To open a support request for this issue, access the IronPort C300V
and issue the "supportrequest" command. The command sends an email with
diagnostic information directly to Cisco IronPort Customer Support to
facilitate a rapid diagnosis of the problem.
Thank you.
MAR logs:
Tue Aug 20 06:56:58 2019 Info: MID: 5223 Attempting to remediate using `bce-demo` profile for recipient [email protected]. Attempt number : 1
Tue Aug 20 06:56:58 2019 Info: MID: 5223 Trying to perform the delete action on Office 365 or Hybrid exchange for SHA256: 993e53a12c43a19e21c3829152d313f0abce4869e1644bc8e60522eb8e637298 recipient's ([email protected]) mailbox.
Tue Aug 20 06:56:59 2019 Info: MID: 5223 Message deleted successfully from [email protected] mailbox.
Tue Aug 20 06:56:59 2019 Info: MID: 5223 Remediation succeeded with `bce-demo` profile for recipient [email protected].
Looking at the ESA report page for Mailbox Auto Remediation:
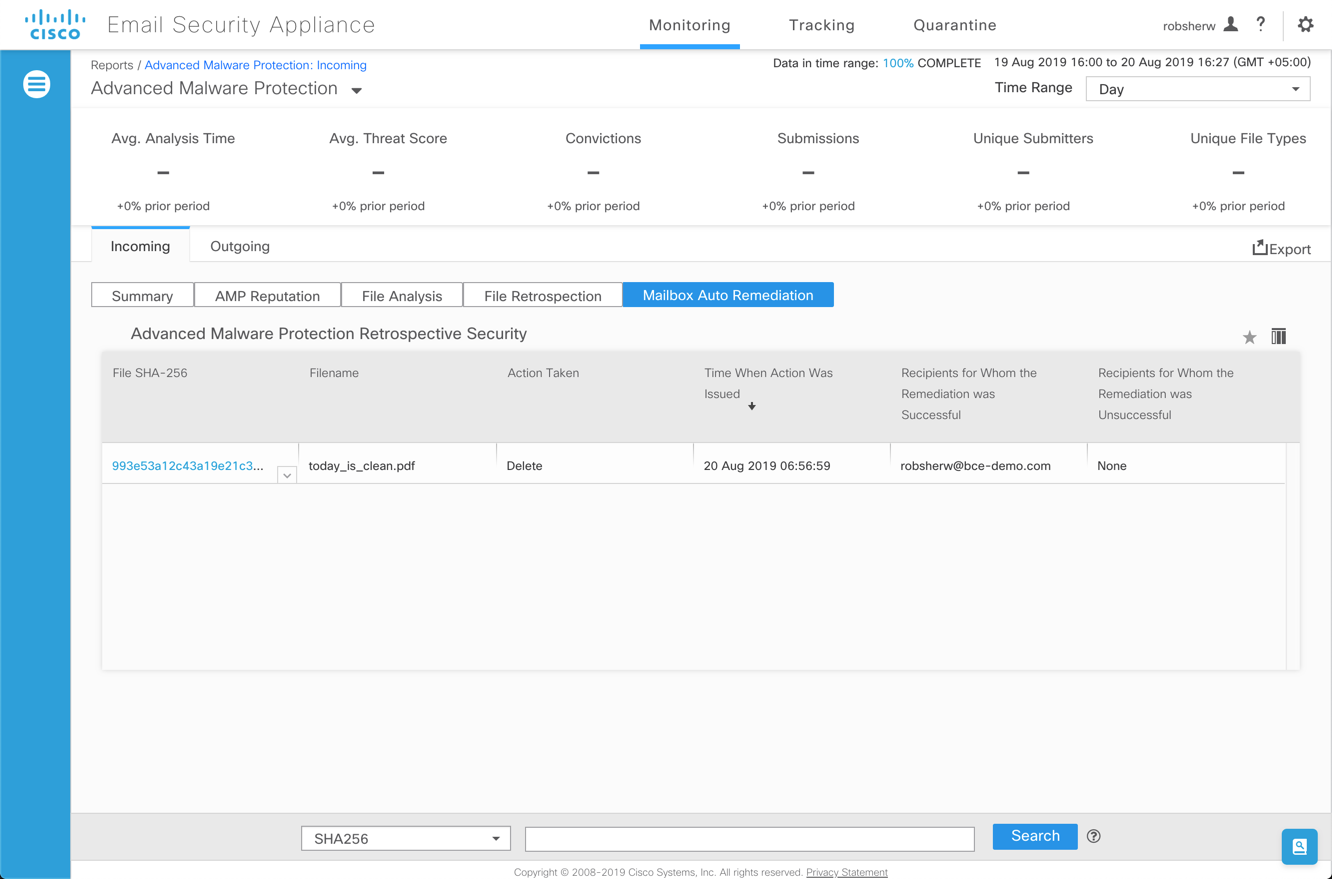
Alerts and Info Messages
Alerts and Info messages are delivered like normal messages. An administrator can parse the mail logs to see the alert sent from the ESA to the administrator(s).
mail_logs/mail.current:Mon Apr 12 10:24:51 2021 Info: Internal SMTP system attempting to send a message to [email protected] with subject 'Info <AMP> esa1.hc3033-47.iphmx.com:AMP Retrospective Alert:monday_1017.xml attachment verdict changed from VERDICT UNKNOWN to MALICIOUS' (attempt #0).
mail_logs/mail.current:Mon Apr 12 10:24:51 2021 Info: Internal SMTP system successfully sent a message to [email protected] with subject 'Info <AMP> esa1.hc3033-47.iphmx.com:AMP Retrospective Alert:monday_1017.xml attachment verdict changed from VERDICT UNKNOWN to MALICIOUS'.
mail_logs/mail.current:Mon Apr 12 10:24:51 2021 Info: A AMP/Info alert was sent to [email protected] with subject "Info <AMP> esa1.hc3033-47.iphmx.com:AMP Retrospective Alert:monday_1017.xml attachment verdict changed from VERDICT UNKNOWN to MALICIOUS".
For Cisco Cloud Gateway administrators, if you are not receiving alerts from your appliance, please open a Cisco Support Case and provide your email address, distribution list, etc., for how you wish to receive the alerts.
Updated about 2 years ago
