Services Updates
Efficacy Guide using Cisco Secure Email
Validate Services and Rules Updates
The Cisco Secure Email Gateway/Cloud Gateway relies on several services with components and rules packages. Each of the services is maintained and updated via the Services Updater. The Services Updater reaches out each five (5) minutes to the Cisco Update Servers by default.
The Rules Updates for each service are reflected via their respective Security Services configuration section.
The main engine that controls the services and aggregates the rules is known as Context Adaptive Scanning Engine (CASE). CASE feeds the following services:
- IronPort Anti-Spam
- Intelligent Multi-Scan (IMS) and Graymail
- Outbreak Filters
Note
In the Updater Logs (updater_logs), 'case' is the component name reflected for all three (3) services listed. Graymail has additional components seen by 'graymail' in the Updater Logs.
From the UI of your Gateway/Cloud Gateway, do the following:
- Security Services > Service Updates
- Scroll down to Automatic Updates
- Assure this is enabled
- Review the configured Update Interval
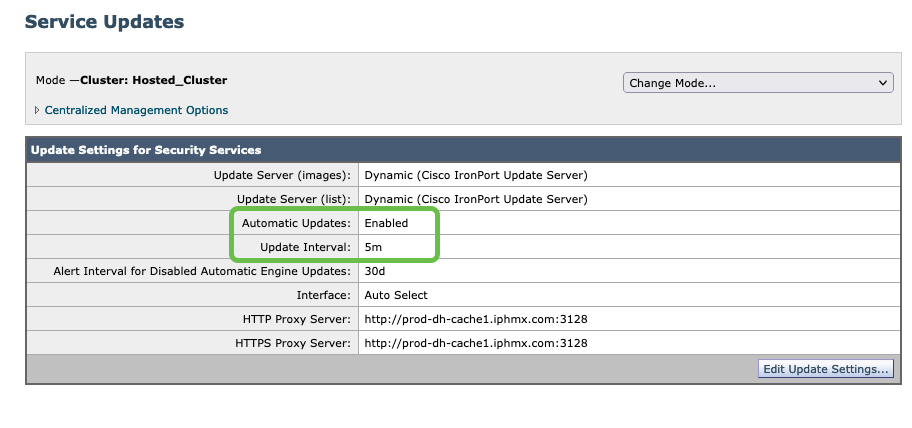
Note: Cluster: Hosted_Cluster as this is Cloud Gateway
From the UI of your Gateway/Cloud Gateway, do the following to update any of the components and rules for the service. This example will use IronPort Anti-Spam:
- Security Services > IronPort Anti-Spam
- Review the Last Update timestamps
- Click Update Now
The other Security Services that rely on on-appliance engines will have the Update Now option.
Note
The process may take a few minutes to sync with the Updater Service. Refresh the page after a few minutes to ensure the timestamps are updated.
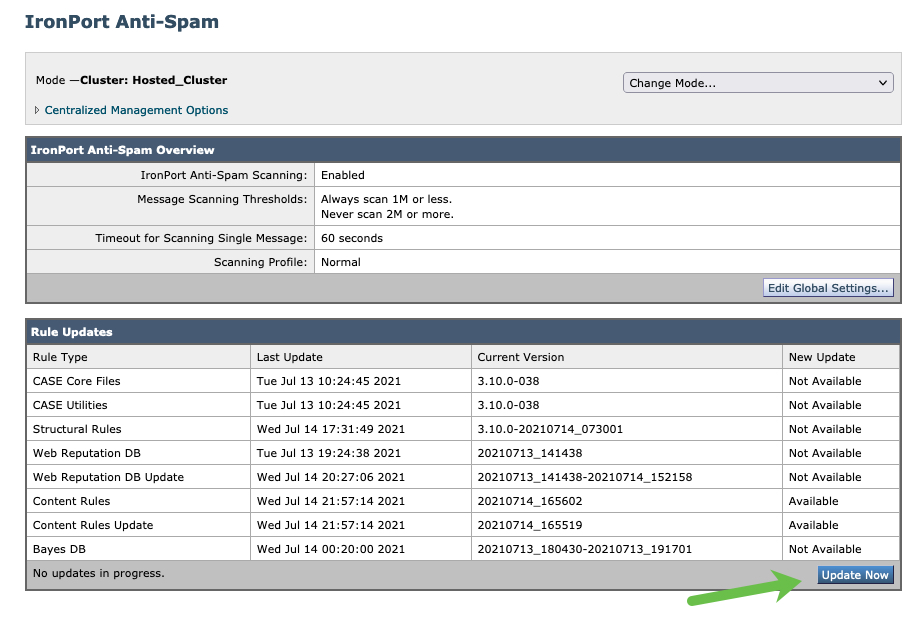
Note: Cluster: Hosted_Cluster as this is Cloud Gateway
If you have CLI access, you can issue the updatenow force command to give an update against ALL services at once. Then, by running tail updater_logs, you will see the process reach out to the Updater Service, and perform the updates.
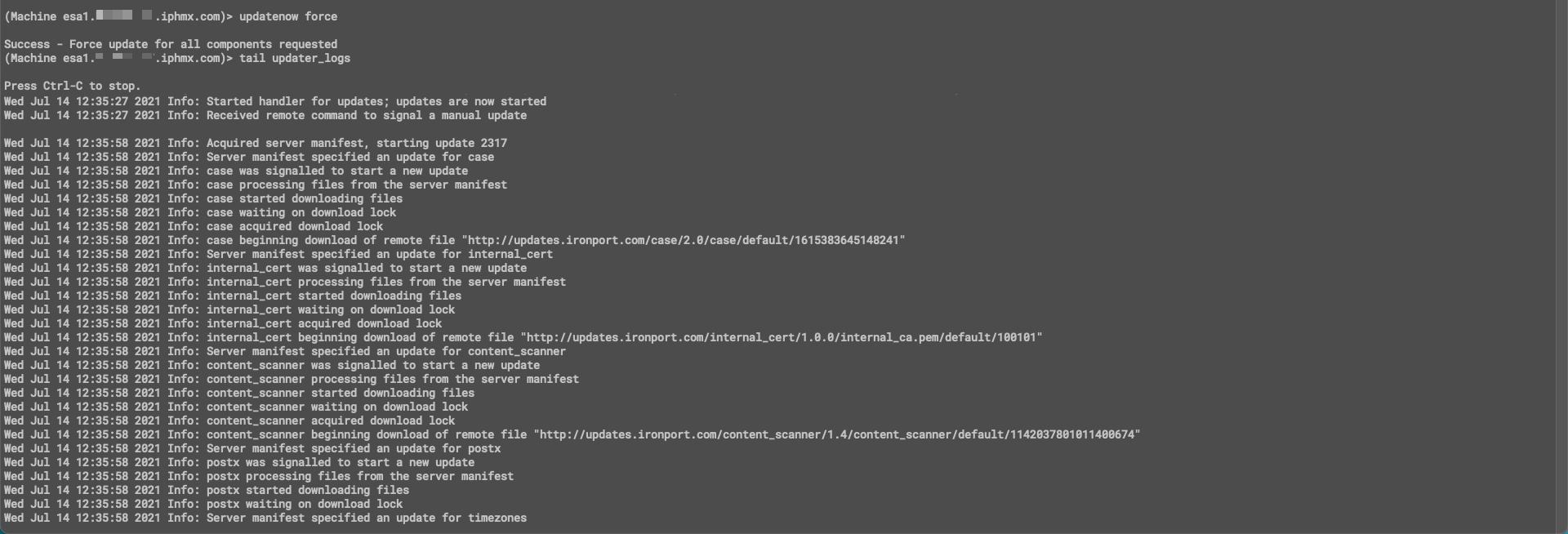
CLI example using 'updatenow force'
Likewise, for each component, there is the option to 'update.' In the example below, for IronPort Anti-Spam, antispamupdate is issued:
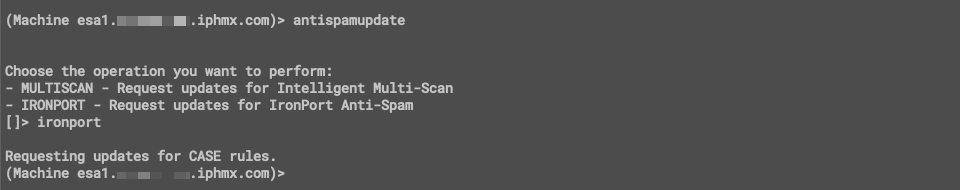
CLI example using 'antispamupdate'
Or, you can run the 'force' update for the component. In the example below, for IronPort Anti-Spam, antispamupdate ironport force is issued:
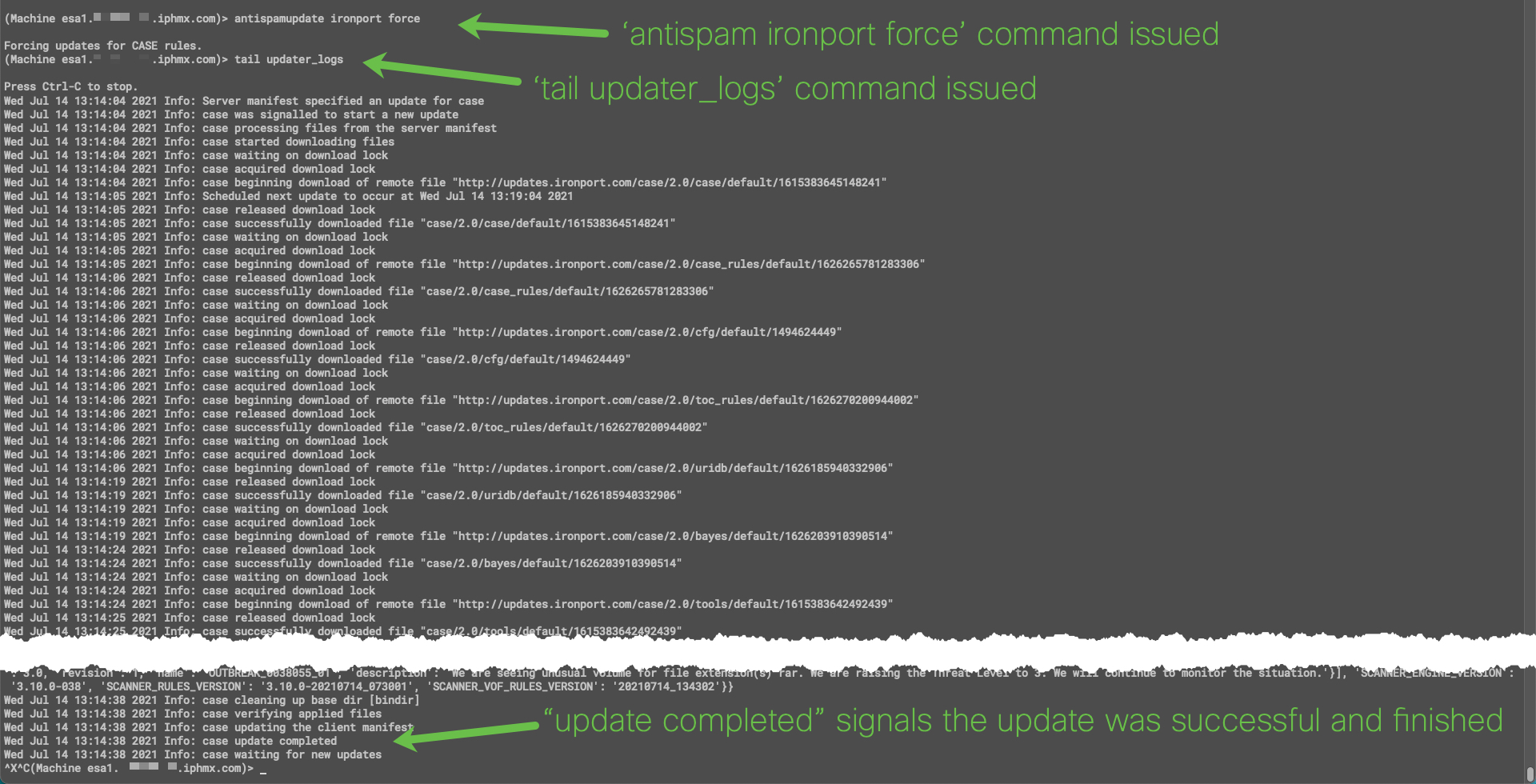
CLI example using 'antispamupdate ironport force'
Using the CLI is not a requirement. For more information on the command line for your version of AsyncOS, see: CLI Reference Guide
Note: Cloud Gateway customers that do not have command line access may request this to be enabled for their instance: Command Line Interface (CLI) Access
FAQ
What is the difference between 'updatenow' and 'updatenow force'?
- 'updatenow' requests an update to all system service components.
- If 'force' parameter is used, update is performed even if no changes are detected.
My security policies do not allow me to directly reach the Updater Server. How do I work around the default configuration for updates?
- If you have a firewall and network limitations, please see: Content Security Appliance Downloads, Updates or Upgrades using a Static Host
- Cisco also offers Updates via local updater/upgrade host for Gateways on an isolated/secure network. Please reach out via a TAC case to get more information.
Guide Checklist
At this time, we have completed the following:
- Introduction
- Services Updates
- Validate Detection Services
- Review of Bypass, Accept or Allow Lists
- Aggressive Profile for Anti-Spam
- Review and Validate MX Records
- Submissions to Talos
- Support Requests
- Security Review (Optional)
Once you have reviewed and updated the services, proceed to the next section of this document.
Updated about 2 years ago
