URL Defense Guide
URL Defense Guide using Cisco Secure Email
About
URLs are seen in emails each day, every day. Not all URLs are safe.
What does Cisco Secure Email do to analyze and protect the end-user from malicious and suspicious URLs? Two options:
- URL Filtering
- URL Rewrite and Analysis (using Outbreak Filters)
Both provide a layered approach to analyzing suspicious URLs and stop malicious URLs from processing through emails.
URLs in incoming and outgoing messages (including attachments) are evaluated. Any valid string for a URL is evaluated, including strings with the following:
- HTTP, HTTPS, or www
- domain or IP address
- a port number preceded by a colon (:)
- uppercase or lowercase letters
When evaluating URLs to determine whether a message is a spam, if necessary for load management, the system prioritizes screening of incoming messages over outgoing messages.
To better understand how URL Filtering and URL Rewrite + Analysis work, let's first take a look at to where they fit in the Email Pipeline within Cisco Secure Email.
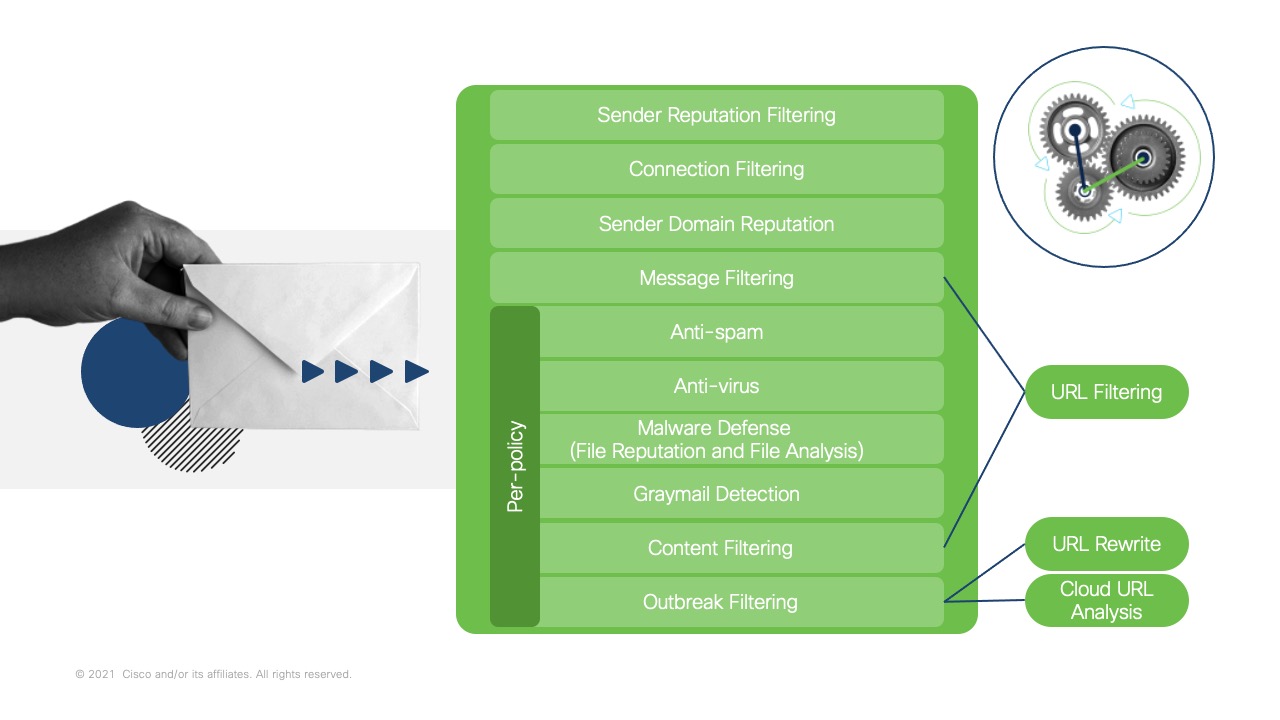
Click the image to enlarge
From the order of processing, URL Filtering happens during Message Filtering or Content Filtering. URL Filtering can be controlled by conditions and actions configured in the Message or Content Filter. We will look at examples of these in URL Filtering.
URL Rewriting is also a function within Outbreak Filters, occurring after URL Filtering.
There are opportunities throughout the mail processing that URL Filtering may catch and detect malicious and suspicious URLs prior to URL Rewrite triggering in Outbreak Filters. This is with help of Talos Intelligence Cloud Services and the microservices that contribute to the service.
Want to know more regarding Cisco Talos Intelligence Cloud Services for URL defense?
- Cisco Talos Intelligence Cloud Services provides URL Analysis.
- Please see Cloud URL Analysis from URL Rewriting and Analysis (using Outbreak Filters).
URL scoring or categorization dispute?
- Please see Reporting Disputes to Cisco Talos
Ready to get started with our best practices for URL Defense?
| 👍 Let's go! |
|---|
Updated about 2 years ago
