URL Rewriting and Analysis Best Practices
URL Defense Guide using Cisco Secure Email
Best Practices with URL Rewriting and Analysis
From our Gold Config + Best Practices we provide the email administrator configuration that Cisco recommends in order to utilize Outbreak Filters for URL defense.
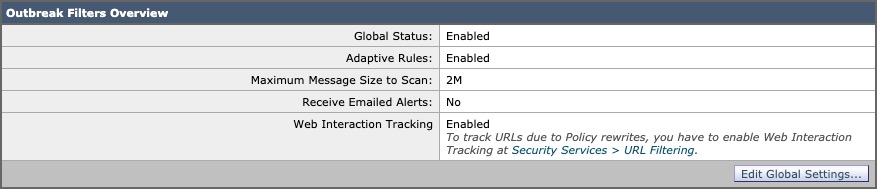
Security Services > Outbreak Filters
- Enable Security Services > Outbreak Filters
- Enable Outbreak Filters Adaptive Rules
- Set maximum message size to scan at 2M
- Enable Web Interaction Tracking
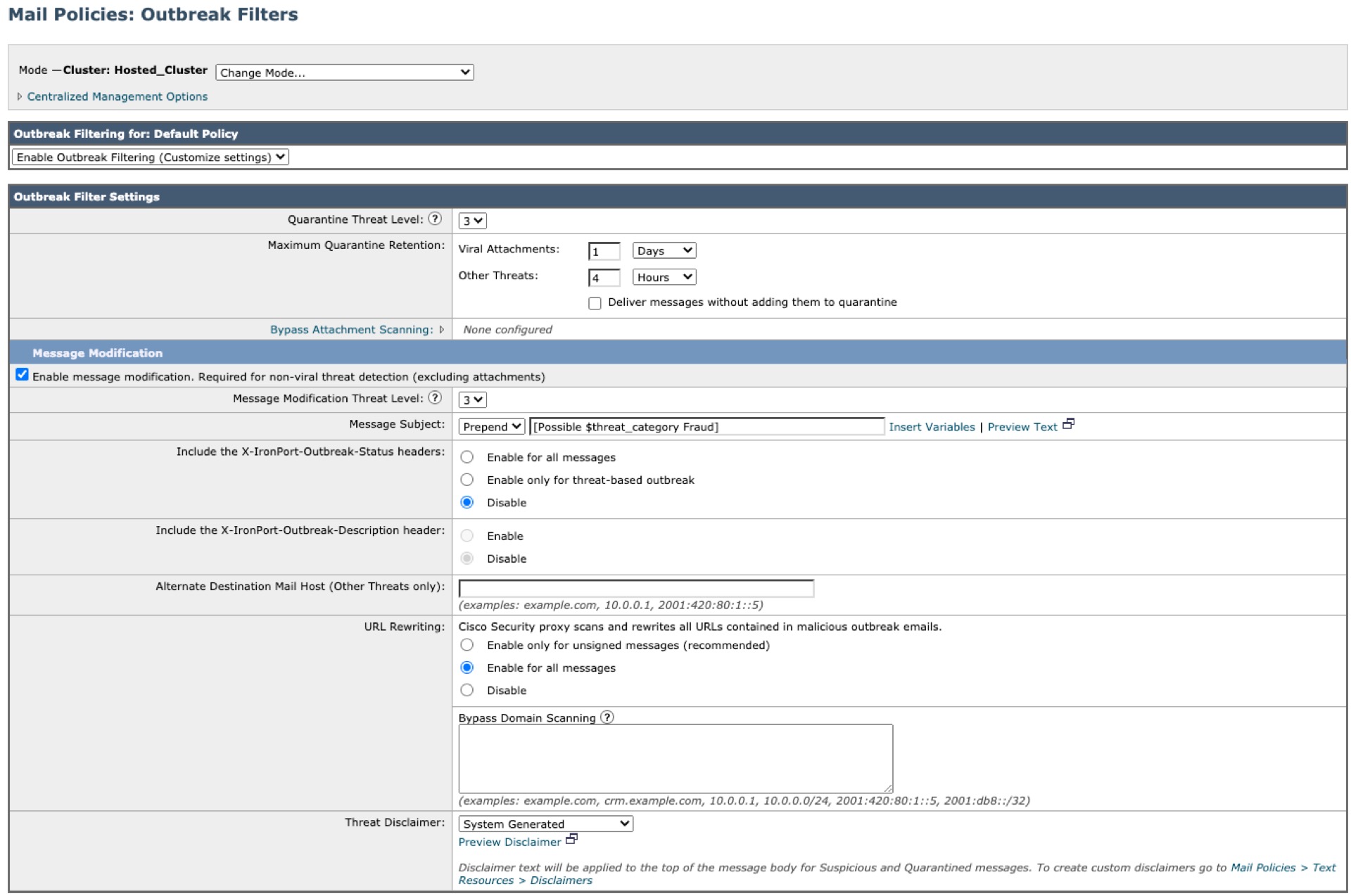
Incoming Mail Policies > Outbreak Filters for Default
- The default threat level is 3, please adjust as per your security requirements
- Quarantine Threat Level: If the threat level for a message equals or exceeds this threshold, the message will be sent to the Outbreak Quarantine. (1=lowest threat, 5=highest threat)
- Enable message modification
- URL Rewriting set for "Enable for all messages"
- Change Subject prepend to [Possible $threat_category Fraud]
- (Optional) Bypass domain scanning
- All destinations and clients in this list will bypass the Cisco Security Proxy.
- Separate multiple entries with commas. Valid formats:
- CIDR addresses such as 10.1.1.0/24, 2001:db8::/32
- An IP address such as 10.1.1.10, 2001:420:80:1::5
- a hostname such as crm.example.com
- a partial hostname such as .example.com
- a domain such as example.com
Updated about 2 years ago
