Validate Detection Services
Efficacy Guide using Cisco Secure Email
Validate Mail Flow Policy Security Features
It is imperative to start at the Mail Flow Policy level. The Security Features section of the Mail Flow Policy should have the following enabled:
- Spam Detection
- AMP Detection
- Sender Domain Reputation Verification
- Virus Outbreak Filters
- Graymail Detection
- Encryption and Authentication
- DKIM, SPF/SIDF, DMARC verification.
Typically this is done by configuring the policy to use the Default policy setting, which should be "On." It is NOT recommended to have these security features configured as "Off."
You may have other Mail Flow Policies created and configured. Please be sure that you have reviewed any Mail Flow Policies that may be named "Accepted," "Allowed," etc., and to assure their Security Features are enabled as described if they are not "Use Default (On)."
Why?
Even if you are NOT taking action based on these security features, the detection capabilities of each service may be used by IronPort Anti-Spam (IPAS) in combination with other detections. Additionally, rules written may take SPF or DMARC into consideration to further process and determine if the message is considered positive spam, suspect spam, or clean. These actions impact processing the message or selecting to block the message.
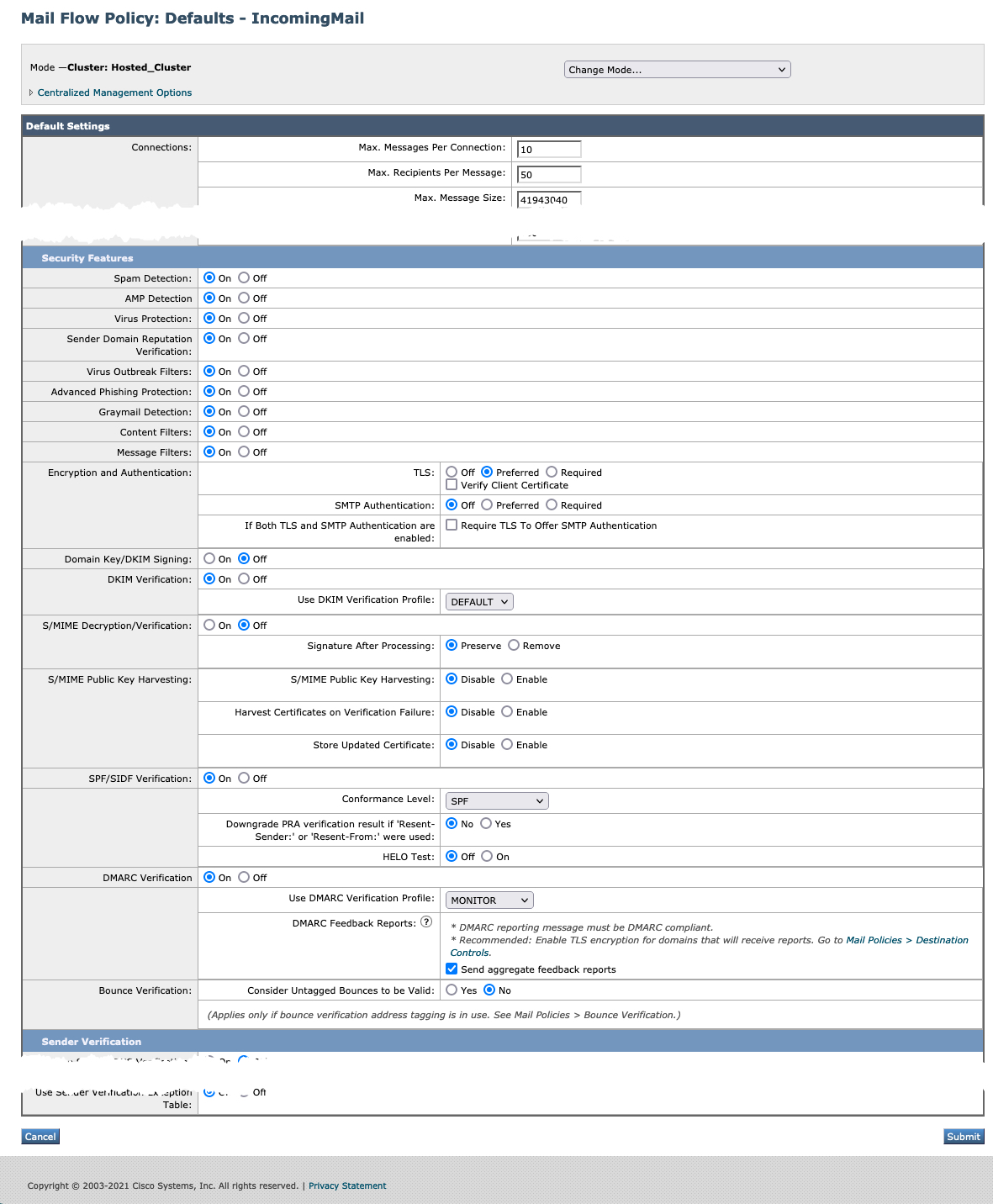
Note: Cluster: Hosted_Cluster as this is Cloud Gateway
Validate Incoming Mail Policies Security Features
Next, review the Incoming Mail Policies. Ensure at the policy level that the features are enabled. These are the services that operate per policy:
- Anti-Spam
- Anti-Virus
- Advanced Malware Protection
- Graymail
- Content Filters
- Outbreak Filters
- Advanced Phishing Protection
Specifically for Anti-Spam, review ANY policy that is not using the default policy settings. This includes the configured actions for how Positively-Identified Spam and Suspected Spam are handled at the policy level. And finally, the Spam Thresholds. Are you using default values or custom settings for the scoring?
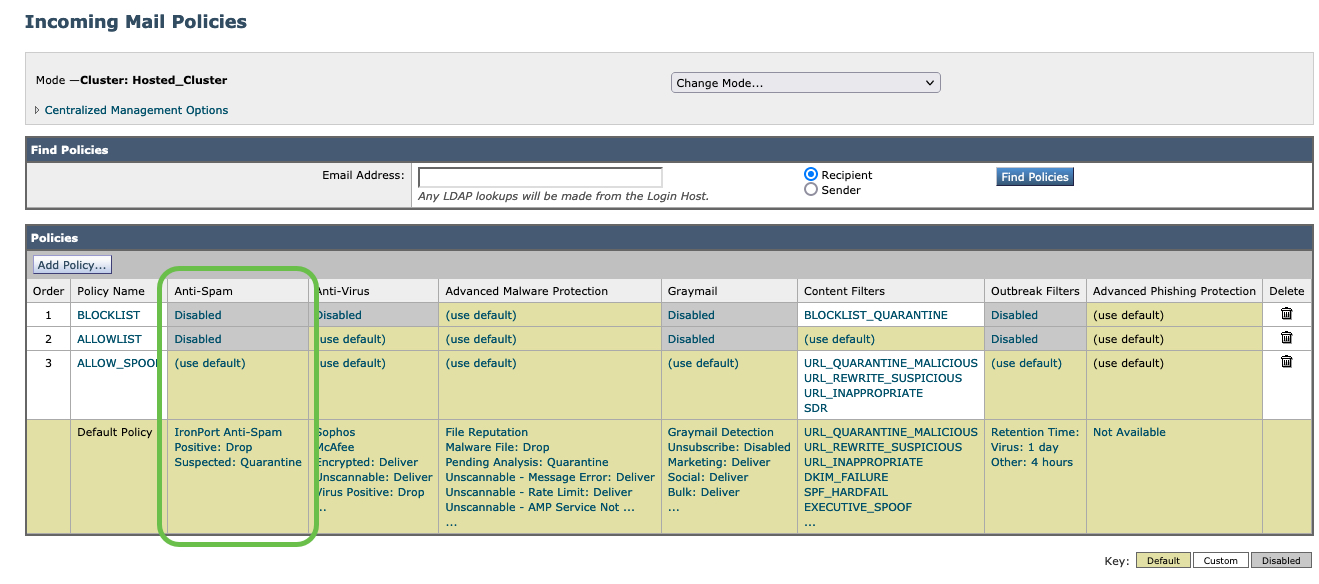
Note: Cluster: Hosted_Cluster as this is Cloud Gateway
Spam Thresholds
What are the defaults for Spam Thresholds?
- For fresh installs, or any appliances that are not running Gold Config + Best Practices, the default is "Use the Default Thresholds," which should be the following:
- Positively Identified Spam: 90
- Suspected Spam: 50
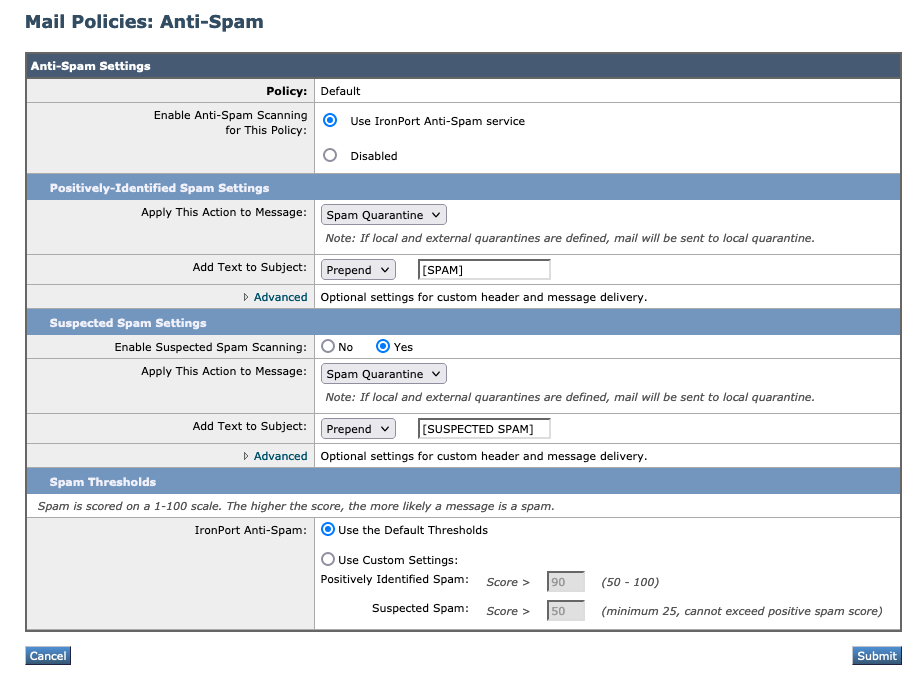
What are the Spam Thresholds if running "Gold Config"?
- Cloud Gateway appliances are pre-configured, running Cisco Best Practices for most customer allocations. Therefore, the Spam Thresholds should be the following:
- Positively Identified Spam: 90
- Suspected Spam: 39
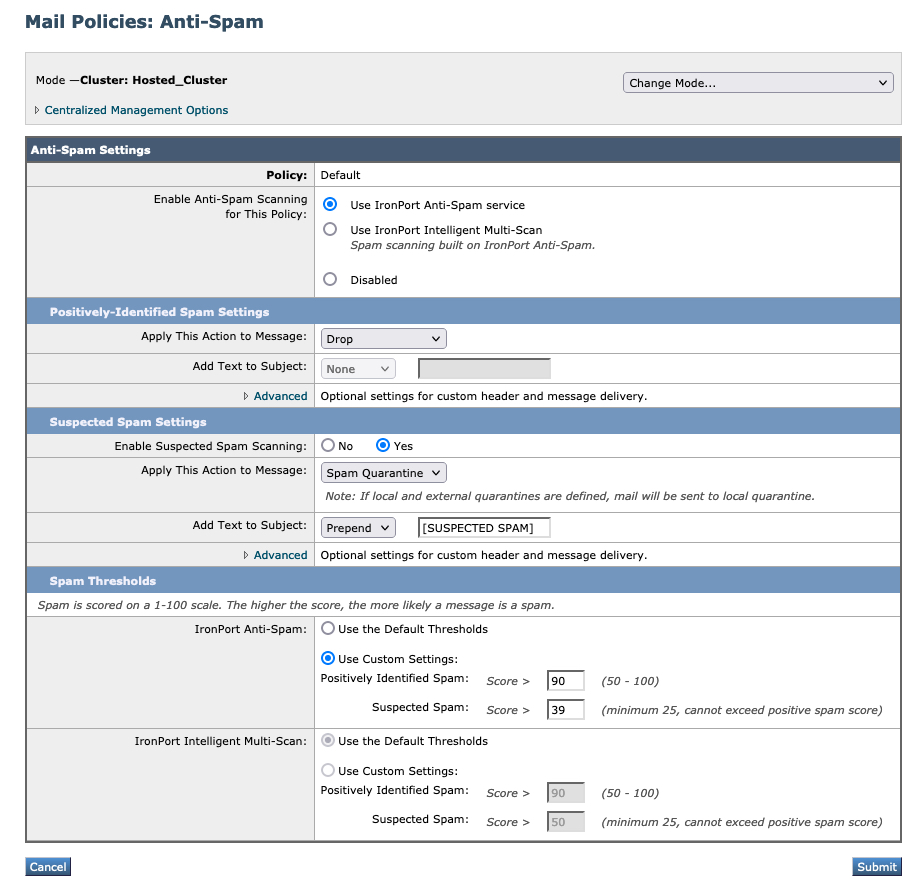
Note: Cluster: Hosted_Cluster as this is Cloud Gateway; IMS is also licensed and shown, but not configured.
Remember
Please remember to submit and commit your changes if you make updates to your Spam Thresholds and configuration.
Note
Cisco does not recommend a more customized approach to Spam Thresholds. Talos implements all rules and thresholds based on the default scoring. The recommendation is to use default or not to skew too far from the default values, as this may impact false positive, false negative occurrences.
More Aggressive Approach
Wanting to be more Aggressive? We will review that coming up in the Aggressive Profile for Anti-Spam section...
Guide Checklist
At this time, we have completed the following:
- Introduction
- Services Updates
- Validate Detection Services
- Review of Bypass, Accept or Allow Lists
- Aggressive Profile for Anti-Spam
- Review and Validate MX Records
- Submissions to Talos
- Support Requests
- Security Review (Optional)
Once you have reviewed and validated the detection services, proceed to the next section of this document.
Updated about 2 years ago
