URL Filtering Best Practices
URL Defense Guide using Cisco Secure Email
Best Practices with URL Filtering
From our Gold Config + Best Practices we provide the email administrator configuration and example content filters that Cisco recommends in order to analyze and stop malicious URLs.
Security Services > URL Filtering
- Enable Security Services > URL Filtering
- Enable URL Category and Reputation Filters
- Enable Web Interaction Tracking in URL Filtering
- Write and enable Content Filters for URL Categorization and Reputation (see below)
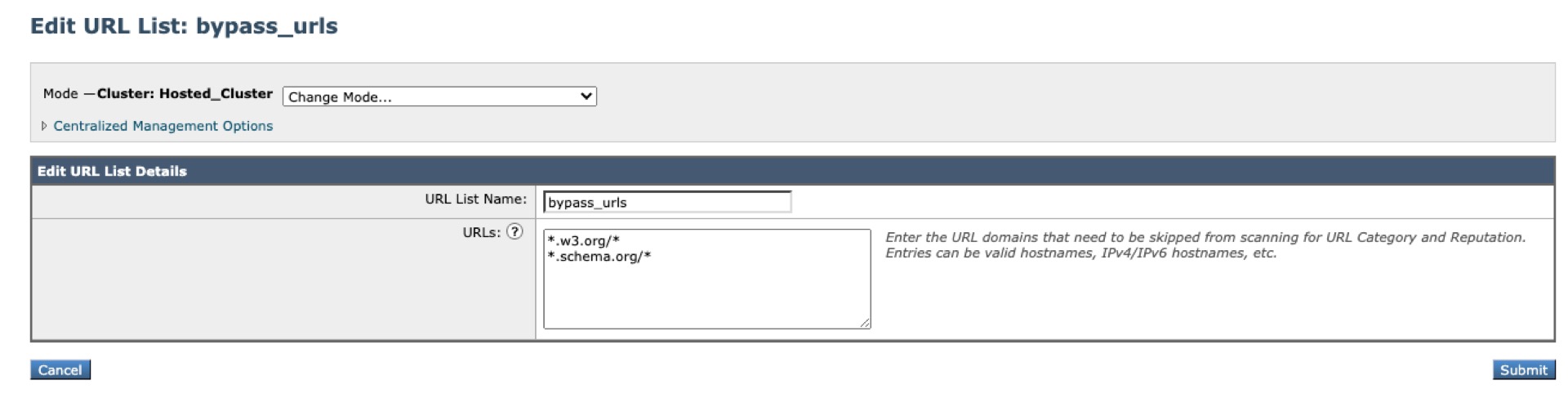
- (Optional) Create and configure URL Allowlist named "bypass_urls"
a. Mail Policies > URL Lists
b. Security Services > URL Filtering > Edit Global Settings... + select your URL List
Click image to enlarge
CLI (websecurityadvancedconfig)
We also recommend the CLI changes for Web Security URL Filtering (websecurityadvancedconfig):
* maximum number of URLs that can be scanned in a message body: 400
* maximum number of URLs that can be scanned in the attachments in a message: 400
* threshold value for outstanding requests: 5
* default time-to-live value (seconds): 600
Note: Starting in AsyncOS 13.5, threshold and time-to-live are default to these settings and no longer appear in the CLI configuration.
Note: Cloud Gateway customers that do not have command line access may request this to be enabled for their instance: Command Line Interface (CLI) Access
CLI (outbreakconfig)
The URL Details tab in Message Tracking requires a config enabled via outbreakconfig, which is CLI only:
myesa.local> outbreakconfig
Outbreak Filters: Enabled
Choose the operation you want to perform:
- SETUP - Change Outbreak Filters settings.
- CLUSTERSET - Set how the Outbreak Filters are configured in a cluster.
- CLUSTERSHOW - Display how the Outbreak Filters are configured in a cluster.
[]> setup
Outbreak Filters: Enabled
Would you like to use Outbreak Filters? [Y]>
Outbreak Filters enabled.
Outbreak Filter alerts are sent when outbreak rules cross the threshold (go above or
back down below), meaning that new messages of certain types could be quarantined
or will no longer be quarantined, respectively.
...
Logging of URLs is currently disabled.
Do you wish to enable logging of URL's? [N]> y
Logging of URLs has been enabled.
Note: Cloud Gateway customers that do not have command line access may request this to be enabled for their instance: Command Line Interface (CLI) Access
Note: This will change with AsyncOS 14.0.1, as this command will be built into the UI and the URL Filtering Security Services configuration.
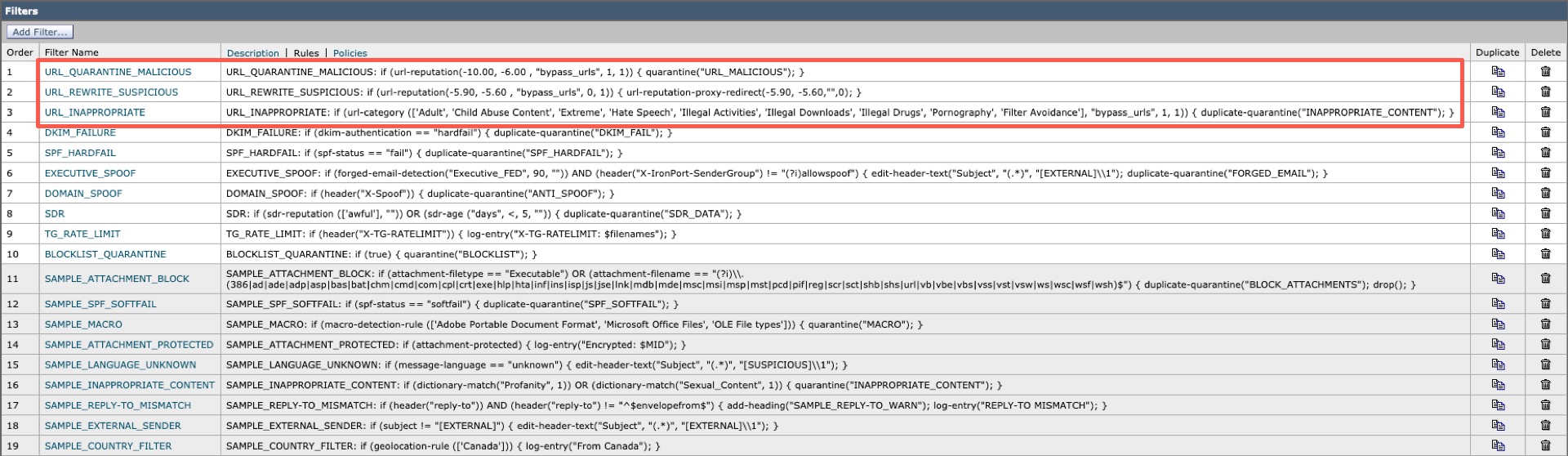
Incoming Content Filters
In the table below, the Content Filters use preconfigured quarantines for URL_MALICIOUS and INAPPROPRIATE_CONTENT. You will need to have these created and committed in your configuration prior to writing the Content Filters.
| Filter Name | Condition | Action |
|---|---|---|
| URL_QUARANTINE_MALICIOUS | URL Reputation; url-reputation(-10.00, -6.00 , "bypass_urls", 1, 1) | Quarantine: quarantine("URL_MALICIOUS") |
| URL_REWRITE_SUSPICIOUS | URL Reputation; url-reputation(-5.90, -5.60 , "bypass_urls", 0, 1) | URL Reputation; url-reputation-proxy-redirect(-5.90, -5.60,"",0) |
| URL_INAPPROPRIATE | URL Category; url-category (['Adult', 'Child Abuse Content', 'Extreme', 'Hate Speech', 'Illegal Activities', 'Illegal Downloads', 'Illegal Drugs', 'Pornography', 'Filter Avoidance'], "bypass_urls", 1, 1) | Quarantine; duplicate-quarantine("INAPPROPRIATE_CONTENT") |
Click image to enlarge
Updated about 2 years ago
