Single Log Line (SLL)
Support for Unified Common Event Format (CEF)-based Logging
The Cisco Email Security appliance now supports a new type of log subscription – ‘Consolidated Event Logs’ that summarizes each message event in a single logline. Using this log subscription, you can reduce the number of bytes of data (log information) sent to a Security Information and Event Management (SIEM) vendor or application for analysis.
The Consolidated Event Logs are in the Common Event Format (CEF) log message format that is widely used by most SIEM vendors.
For more information, see the “Logging” chapter in the user guide.
SLL: configuration
- System Administration > Log Subscriptions
- Add Log Subscription...
- Select the log type as Consolidated Event Logs
- Select the fields that you want in the consolidated event log
- Select a log retrieval mechanism for the log subscription
- Submit and commit your configuration changes
NOTE
CLI configuration not available for “Consolidated Event Logs”
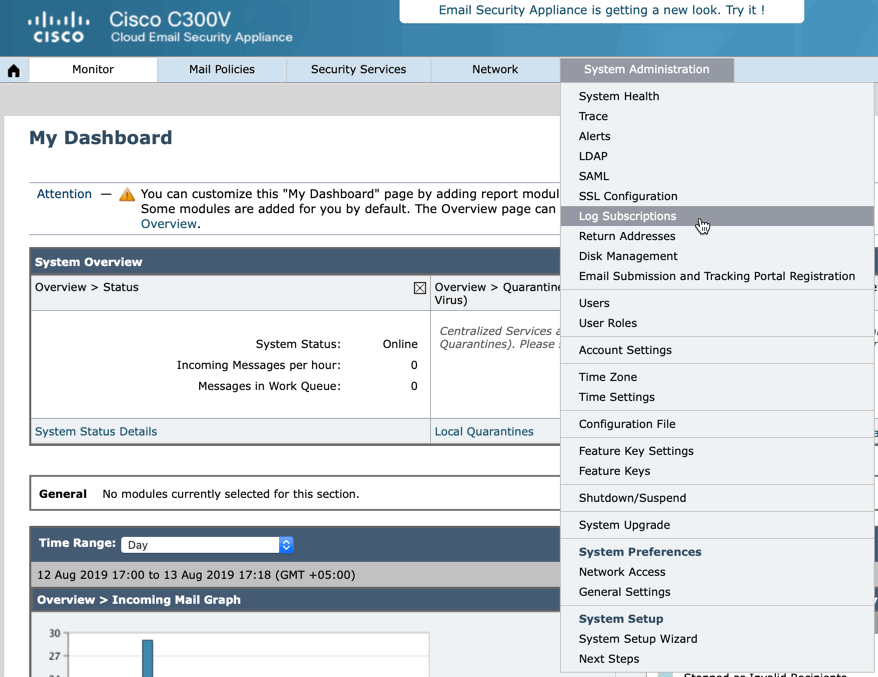
System Administration > Log Subscriptions
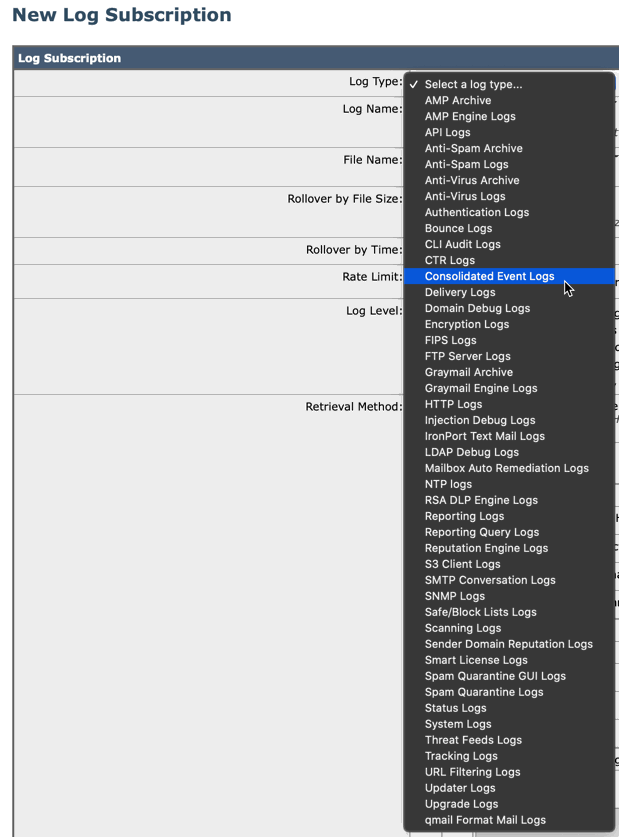
Add Log Subscription...
And select Consolidated Event Logs
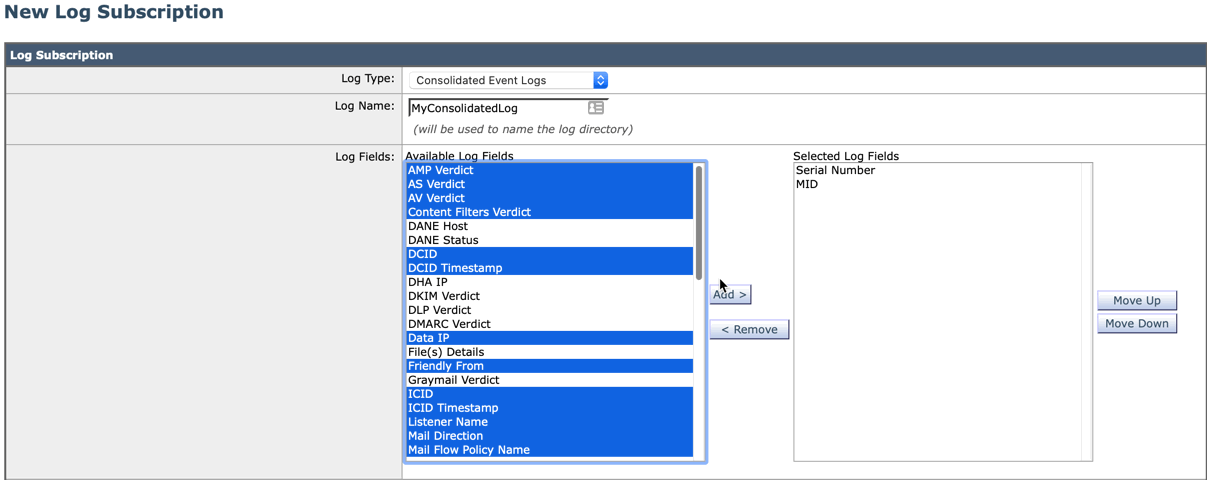
Enter in a log name
Choose the Log Fields and set the order of events
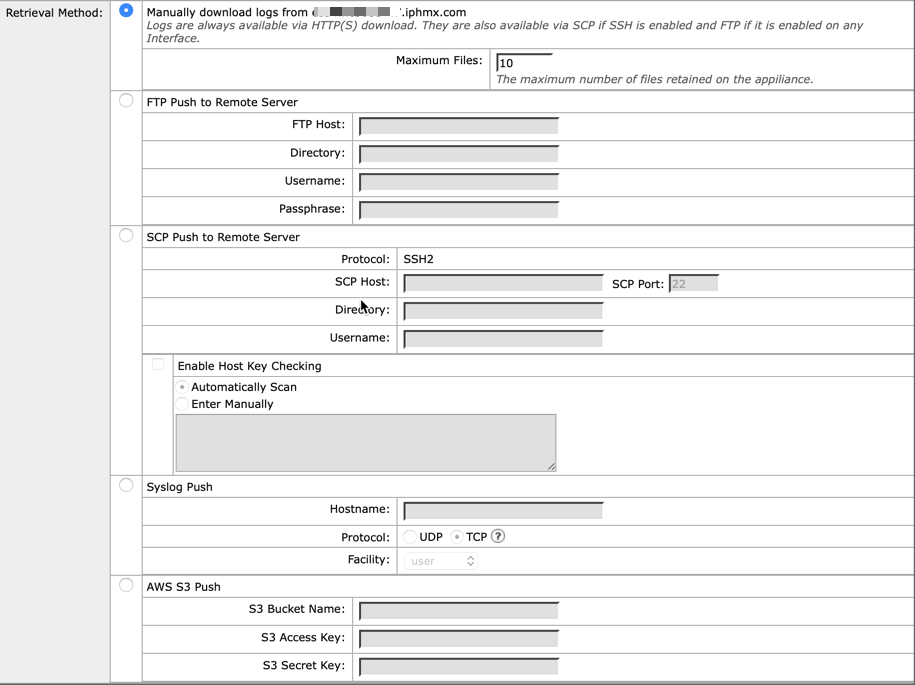
Select your Retrieval Method
[NEW AWS S3 Push]
SLL: log example
With the set variables in the log subscription configuration, once SLL is enabled, you will see similar to the following:
Tue Aug 13 15:15:49 2019: CEF:0|Cisco|C300V Email Security Virtual Appliance|13.0.0-252|ESA_CONSOLIDATED_LOG_EVENT|Consolidated Log Event|5|deviceExternalId=420D4F36AAEBC0093B4F-B9E72189A021 ESAMID=4631 ESAAMPVerdict=SKIPPED ESAASVerdict=NEGATIVE ESAAVVerdict=NEGATIVE ESACFVerdict=MATCH ESADCID=66096 endTime=Tue Aug 13 15:15:48 2019 ESADKIMVerdict=pass ESADLPVerdict=NOT_EVALUATED ESADMARCVerdict=pass dvc=140.140.140.140 [email protected] ESAGMVerdict=NEGATIVE ESAICID=36050 startTime=Tue Aug 13 15:15:45 2019 deviceDirection=0 ESAMailFlowPolicy=ACCEPT suser=bounce-md_30372747.5d528dcf.v1-d57275a6c9df40418a90fd977e3bf506@mandrill.appc.cisco.com cs1Label=MailPolicy cs1=DEFAULT cs2Label=SenderCountry cs2=United States ESAMFVerdict=MATCH act=BOUNCED ESAFinalActionDetails=5.1.0 - Unknown address error cs4Label=ExternalMsgID cs4='<[email protected]>' ESAOFVerdict=NEGATIVE [email protected] ESAHeloDomain=someesa.iphmx.com ESAHeloIP=139.139.139.139 cfp1Label=SBRSScore cfp1=0.9 ESASDRDomainAge=9 years 3 months 14 days cs3Label=SDRThreatCategory cs3=N/A cs6Label=SDRRepScore cs6=Neutral ESASPFVerdict=SoftFail sourceHostName=esa1.hc3033-47.iphmx.com ESASenderGroup=GREYLIST sourceAddress=139.138.56.31 msg=Cisco=20Advanced=20Phishing=20Protection=20System=20Notification=20for=20bce-demo ESATLSInCipher=ECDHE-RSA-AES128-GCM-SHA256 ESATLSInConnStatus=Success ESATLSInProtocol=TLSv1.2 ESATLSOutCipher=ECDHE-RSA-AES256-SHA384 ESATLSOutConnStatus=Success ESATLSOutProtocol=TLSv1.2 ESAURLDetails={'https://bce-demo.appc.cisco.com/sensors/a7b04388-0f6e-11e9-8def-0242ac110002': {'Category': 'Computers and Internet', 'WbrsScore': '7.3'}, 'http://mandrill.appc.cisco.com/track/open.php?u=30372747&id=d57275a6c9df40418a90fd977e3bf506': {'Category': 'Computers and Internet', 'WbrsScore': '7.3'}} deviceInboundInterface=IncomingMail
SLL: AWS S3
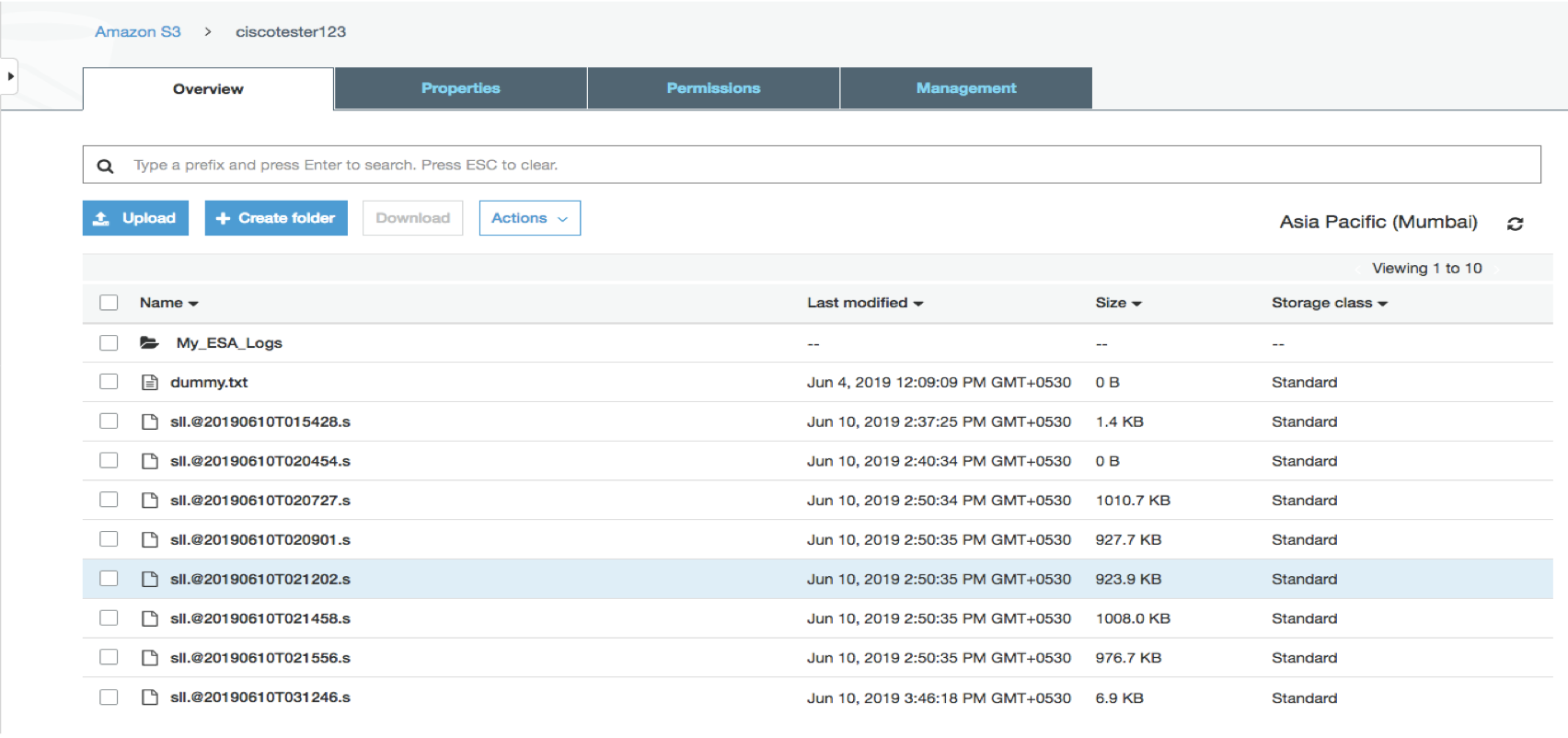
Example of SLL log transferred to AWS S3
S3 Client logs
When AWS S3 Push is configured, the s3_client log is enabled recording communication between the ESA and AWS bucket:
Fri Jul 26 16:35:26 2019 Info: S3_CLIENT: Server started
Fri Jul 26 16:35:26 2019 Info: S3_CLIENT: Uploading files to S3 Bucket example.com for the subscription: consolidated_logs
Fri Jul 26 16:35:26 2019 Info: S3_CLIENT: Completed uploading files to S3 Bucket example.com for the subscription: consolidated_logs
Fri Jul 26 16:35:26 2019 Info: S3_CLIENT: No pending uploads. Will reattempt uploads in 10 minutes
Fri Jul 26 16:43:17 2019 Info: S3_CLIENT: Server started
Fri Jul 26 16:43:18 2019 Info: S3_CLIENT: Uploading files to S3 Bucket example.com for the subscription: consolidated_logs
Fri Jul 26 16:43:18 2019 Info: S3_CLIENT: Completed uploading files to S3 Bucket example.com for the subscription: consolidated_logs
Fri Jul 26 16:43:18 2019 Info: S3_CLIENT: No pending uploads. Will reattempt uploads in 10 minutes
Any errors in communication will be logged to the s3_client log:
Tue Aug 13 18:25:41 2019 Info: S3_CLIENT: Uploading files to S3 Bucket example.com for the subscription: MyConsolidatedLog
Tue Aug 13 18:25:41 2019 Warning: S3_CLIENT: ERROR: Upload Failed to S3 bucket example.com. Reason: Failed to upload /data/pub/MyConsolidatedLog/[email protected] to example.com/[email protected]: An error occurred (InvalidAccessKeyId) when calling the PutObject operation: The AWS Access Key Id you provided does not exist in our records.
Tue Aug 13 18:25:41 2019 Warning: S3_CLIENT: Completed uploading files to S3 Bucket example.com with one or more failures for the subscription: MyConsolidatedLog.
Upload failed for the following:
[u'[email protected]']
ESA administrators who have alerts enabled will receive alerts via email.
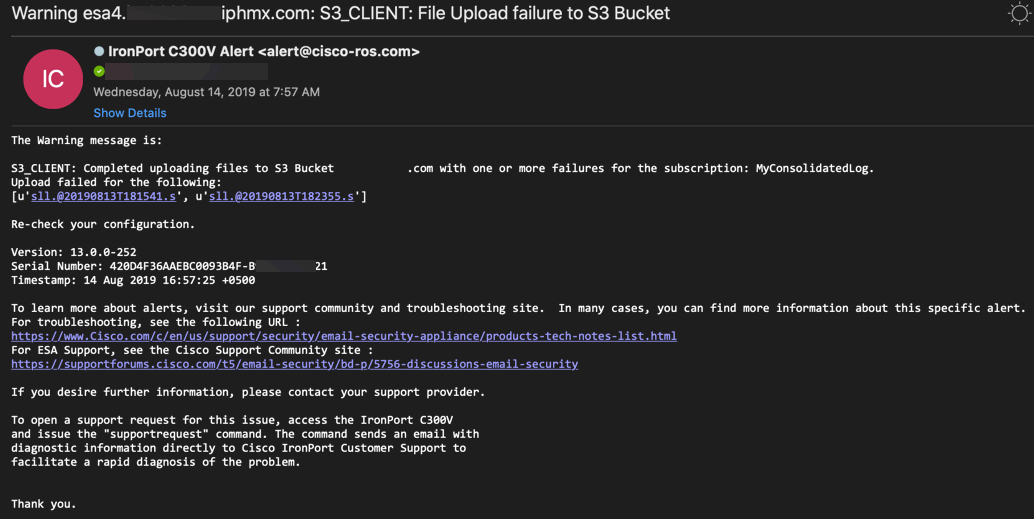
Example Warning alert notification
SLL: debugging
Consolidated Event Logs will not get generated in the following scenarios:
- When SMTP routes are missing for Receiving Domain
- Receiving domain with Invalid Destination Host information
- When Destination Hosts is down which provided by the admin
We will not populate Log fields in SLL Logs which results as “NA” even though the user has selected that particular log fields.
Log Fields (Event verdicts) of “Consolidated Event logs” will get a result as “NA” in the following scenarios:
- When the feature is not enabled
- When feature key is not available for the particular security feature
Updated about 2 years ago
