Cisco Secure Email Informational Announcement - Certificates
What
Cisco Secure Email is committed to delivering the best possible service to our customers. For the last several years, Cisco has been issuing SSL certificates for its infrastructure through a partner company, HydrantID. The certificate chain for those certificates includes an intermediate CA operated by HydrantID which is signed by the QuoVadis Root CA 2—this root CA is owned and managed by a separate company, QuoVadis Global. Up to this point, Cisco products could enable trust in Cisco infrastructure and services by incorporating trust in the QuoVadis Root CA 2.
As of mid-2020, QuoVadis was acquired by DigiCert. In light of this acquisition, DigiCert has begun making plans to cease new cert issuance from the QuoVadis root Cisco uses, moving customers elsewhere. In light of these acquisitions and corresponding business relationship changes, Cisco needs to migrate our SSL issuance to a new HydrantID issuing CA that is signed by IdenTrust (who purchased HydrantID in 2020). The effect of this on Cisco products and infrastructure is that any infrastructure that does not trust the IdenTrust root will no longer be able to connect to critical Cisco infrastructure.
PSIRT bug CSCvx00430 is addressed in AsyncOS 13.7x and CES has started mass upgrades. If your CES instance is not upgraded to 14.x, please reach out to TAC to get your instance upgraded addressed.
When
Starting March 1, 2021
Monday-Friday:
Europe Window: 6 PM to 2 AM (London)
Canada Window: 6 PM to 2 AM (Kamloops)
Americas Window: 6 PM to 2 AM (San Francisco)
APJ Window: 6 PM to 2 AM (Tokyo)
Update
- IdenTrust – CA 01 must be added CES Cert Store. (Done)
- IdenTrust – CA 01 certificate will be placed at the cluster level. A QuoVadis (G2/G3) should continue to work but customers are advised to update to IdenTrust – CA 01. (After April 5, 2021)
Customer Action
Customers should review the use of their existing certificate and replace it with the new IdenTrust – CA 01 certificate which is at the cluster level. Any machine-level certificate configurations must be deleted to allow the use of the new certificate.
Customer Impact
Existing QuoVadis (G2/G3) certificates will continue to work normally till their natural expiration date. After April 5, IdenTrust – CA 01 certificates will be available.
Expected Impact
There should not be any email delivery disruption. New certificates will be placed at the cluster level.
If you have any urgent questions about this maintenance or the possible impact, please contact Cisco TAC.
Advanced Customer Information
Do you want to check your certificate?
- Use CheckTLS's testTo
- For the email target, use "[email protected]" [where hcXXYY is your ESA1 hostname as seen from your My Dashboard when logging in via the UI.]
- For Output Format use "CertDetail"
- Click Run Test
The output will be similar to the following:
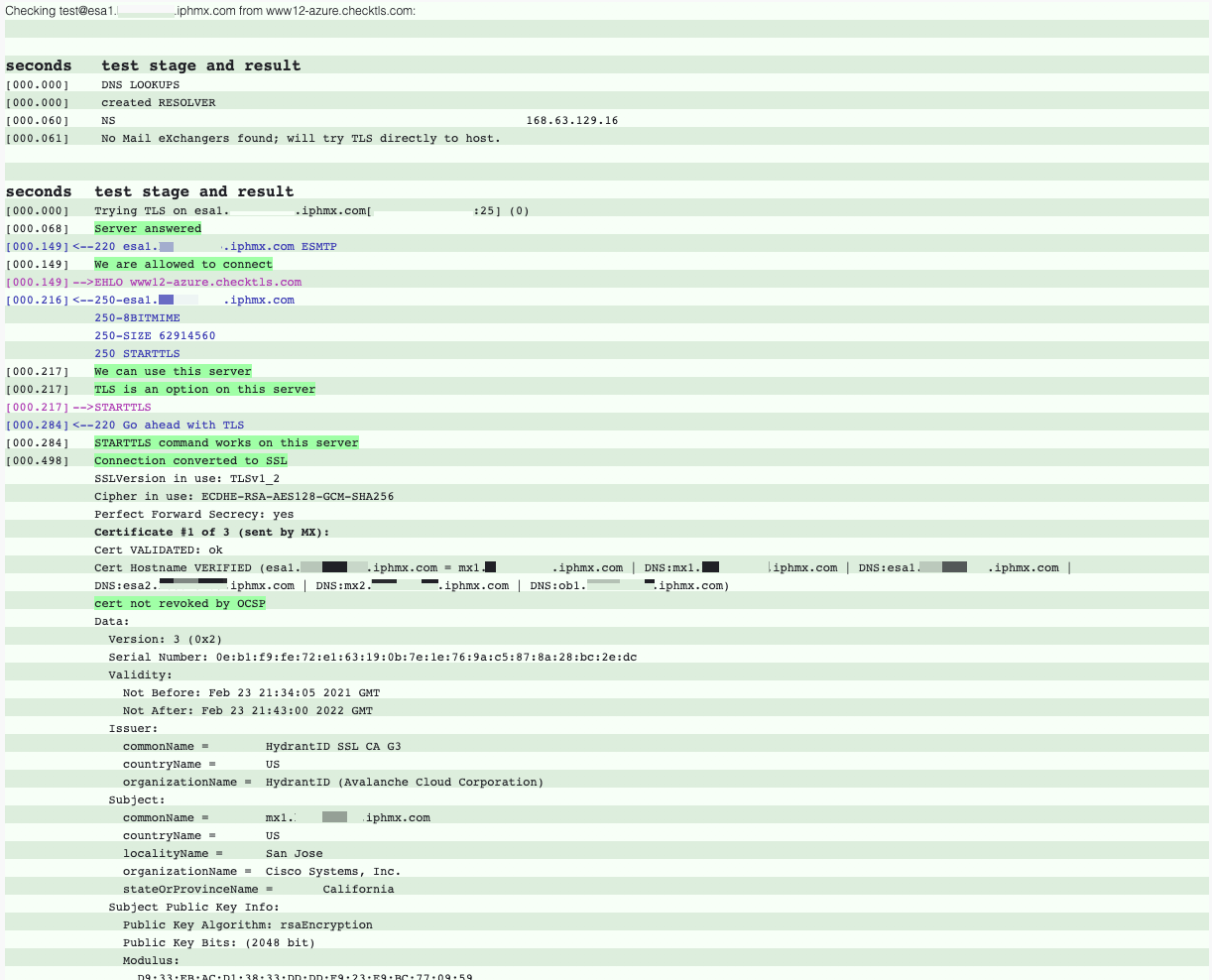
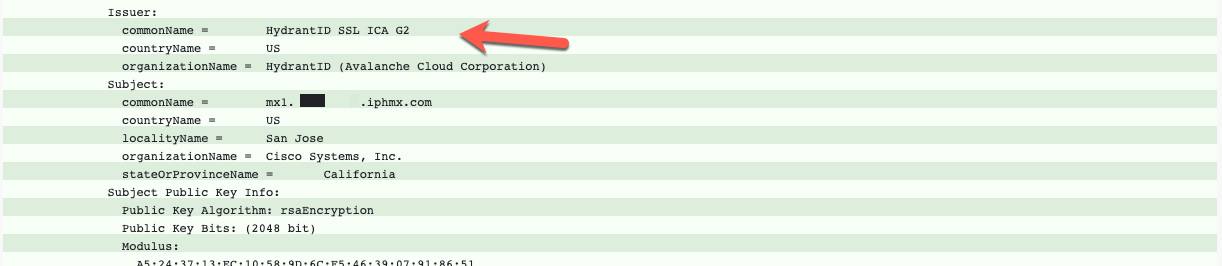
What you will want to confirm is located in the Issuer section of the output:
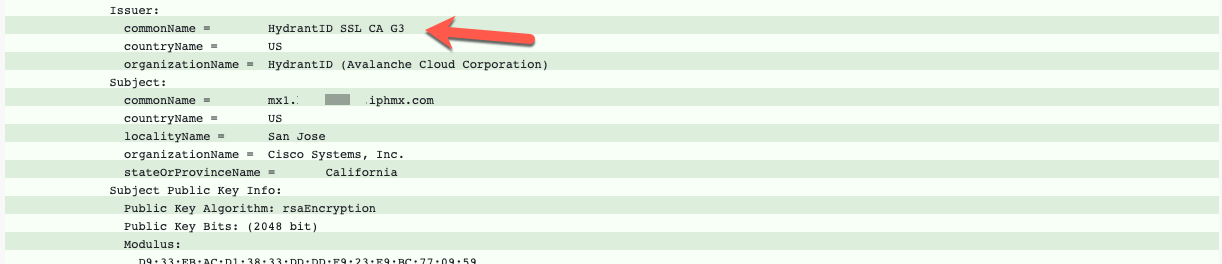
In the example above, when using CheckTLS, if you see G3, your certificate has been updated. CES Ops have also begun the rollout of CA 01 certificates. You will also see the certificate information on the user interface of your appliance.
From your Secure Email Cloud Gateway (ESA) check the following:
- Log in to the ESA UI
- Click Network > Certificates
- You will see similar:
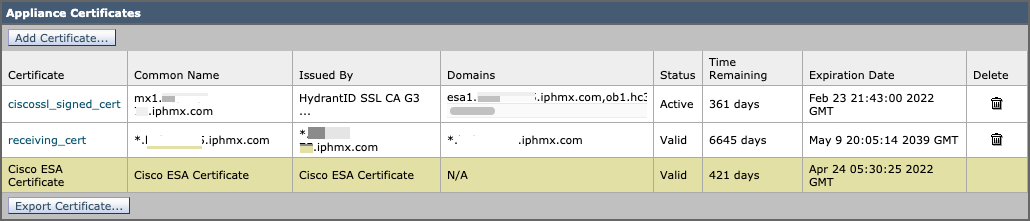
Clicking into the 'ciscossl_signed_cert' will show you the Root Certificate and Intermediate Certificate (when applicable):
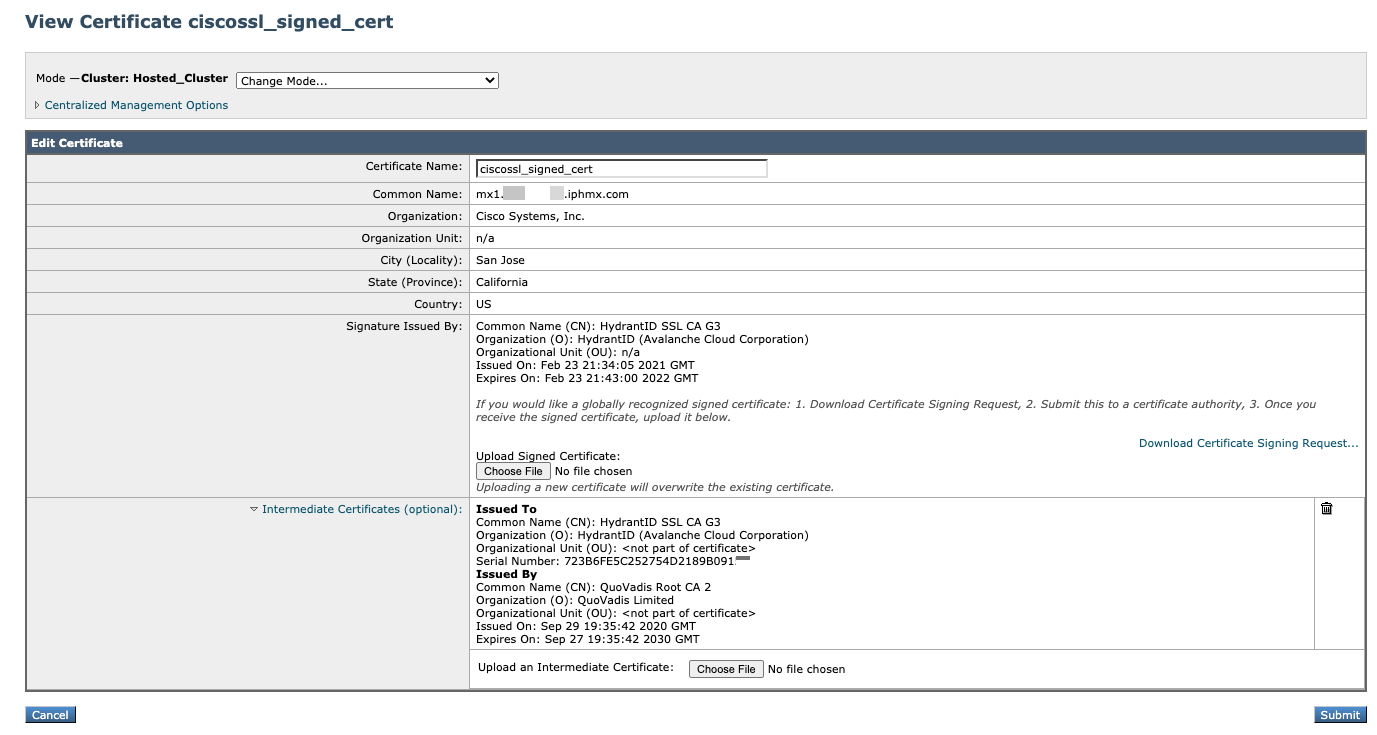
Showing G3 Certificate
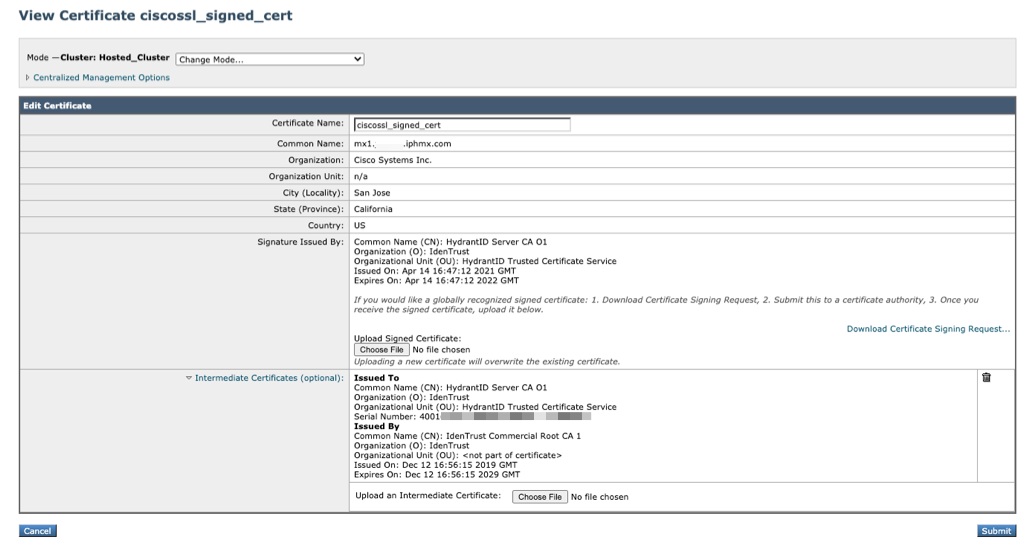
Showing CA 01 Certificate
Note
If your configuration has certificates for Group or Machine-mode settings in addition to certificates in Cluster, you may need to check your configuration based on that level of configuration. Please click into Change Mode... to access the dropdown for managing any alternate certificate configuration.
When using CheckTLS, if you see G2, your certificate has not been updated:
From your Secure Email Cloud Gateway (ESA) check the following:
- Log in to the ESA UI
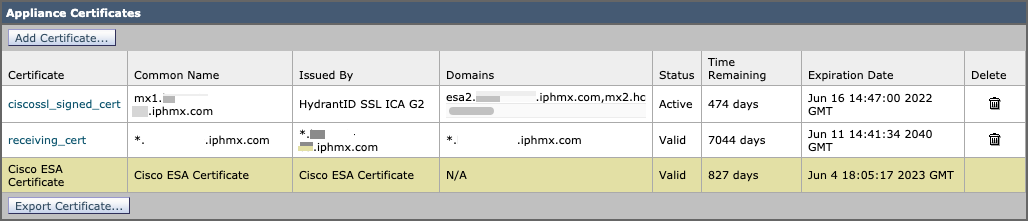
- Click Network > Certificates
- You will see similar:
Clicking into the 'ciscossl_signed_cert' will show you the Root Certificate and Intermediate Certificate (when applicable):
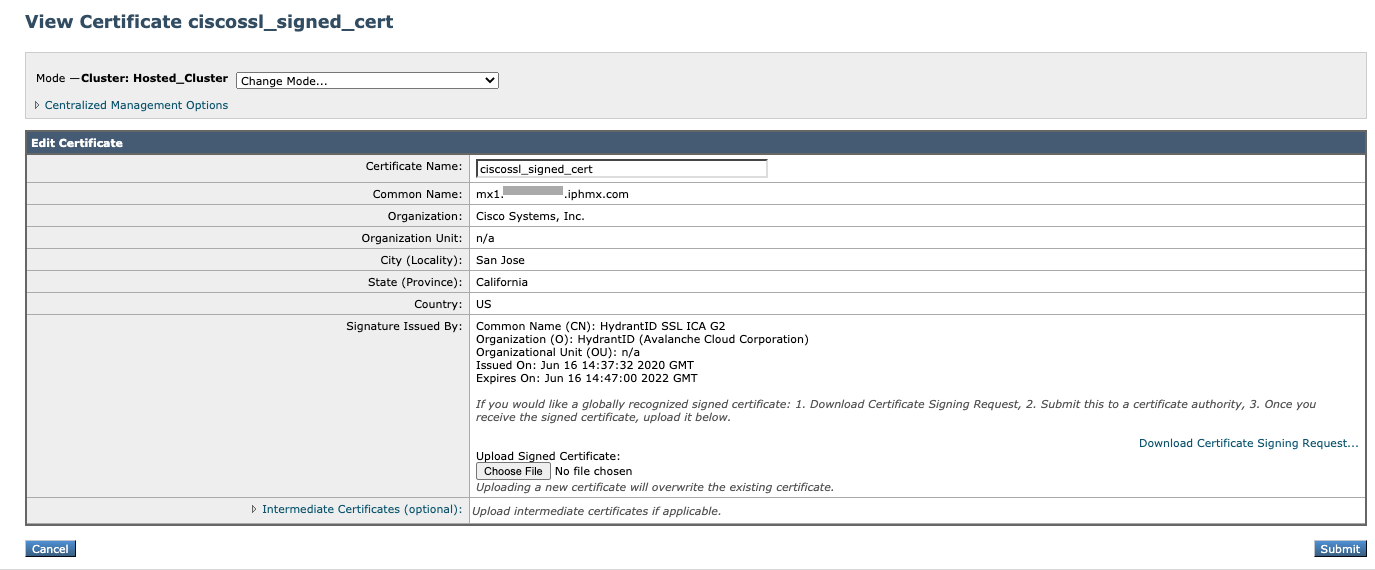
Again, if you have any urgent questions about this maintenance or the possible impact, please contact Cisco TAC.
More Resources + Information
Updated almost 2 years ago
Need to know more about certificates on Cisco Secure Email Cloud Gateway?
